What is HydraCrypt Ransomware?
The HydraCrypt Ransomware is a Trojan that is utilized by hackers to lock the files of contaminated users and in return demands ransom for releasing the decryption key. The HydraCrypt cryptomalware is sent to users who is utilizing the Angler Exploit Kit, which is stacked on a remote server.
A few compromised websites are known to proliferate the HydraCrypt Ransomware among which are Drivers-softprotect.eu, Vyetbr.tk and Harbourfrontcentre.com. Numerous contaminations with the HydraCrypt Ransomware are encouraged with the Botime Trojan-Dropper that may plant the executable of the HydraCrypt Ransomware in the System32 file under the Windows catalog. Malware analysts take note of that the HydraCrypt Ransomware is moderately basic in conduct and is like the Buddy Ransomware. Once the users has been tainted with the HydraCrypt Trojan, it would enlist itself to be keep running on the following system boot up. The encryption procedure would keep running in background while the user is surfing the Internet and playing games.
The HYDRACRYPT ransomware focuses on all versions of Windows including:
- Windows XP
- Windows vista
- Windows 7
- Windows 8
- Windows 10
Is Paying Ransom is enough to get your files back?
Despite the fact that we highly suggest not paying the ransom, paying the ransom will be the only option to advance their business and you will only boost their confidence. The files contain a message advising casualties of the encryption and urges them to pay ransom for decrypted data. These hackers at that point request a ransom in return for decoding. The cost which they asked is $400 in Bitcoins. It is presently unsubstantiated which encryption calculation they utilizes, since any way decryption requires a unique key, which is put away on a remote server controlled by digital crooks. Despite the fact that you might be urged to pay, digital culprits can't be trusted. These hackers usually overlook casualties, once the ransom is submitted, and there is a high chance that you will fall into their scam trap. You will lose your cash and bolster digital crooks' evil plans. Therefore, we unequivocally encourage you to overlook all request to contact these individuals or pay any payment.
Here is a screenshot of Ransom note:
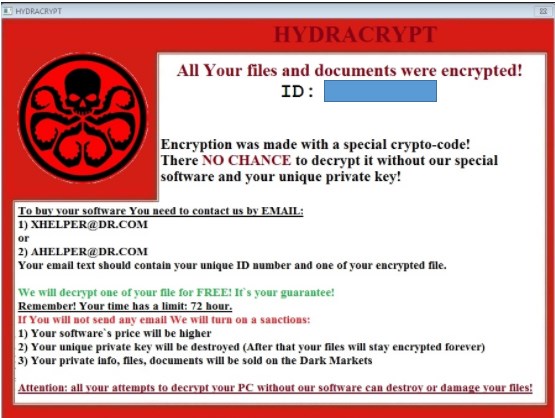
HYDRACRYPT Ransomware- What does it do.
The email address can be found in a TXT file named README_DECRYPT_HYDRA_ID_ that is placed in every folder containing the .HYDRACRYPT files inside. This contamination came in notice because of how it encodes the user's files– specifically, it utilizes AES-265 and RSA encryption technique – keeping in mind the end goal to guarantee that the influenced users must choose the option to buy the private key. At the point when the HYDRACRYPT ransomware is first introduced on your PC, it will make a random named executable in the %AppData% or %LocalAppData% organizer. This executable will be driven and start to scan all the drive letters on your PC for information file to encode.
HYDRACRYPT ransomware scans for documents with certain file extension to encrypt. The data it encodes incorporate essential efficiency reports and documents, for example, .doc, .docx, .xls, .pdf, among others. At the point when these documents are identified, this contamination will change the extension to .hydracrypt_ID_[8 random characters], so they are not any more ready to be opened.
Here is a Screenshot of Files Encrypted by the Hydracrypt Ransomware.

Temporarily Disable HYDRACRYPT Ransomware in Safe Mode with Command Prompt
Step – 1 (enter safe mode)
- Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shutdown, then restart.
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next and followed by yes.
Download Free Removal Tool
How does HYDRACRYPT Ransomware gets on to your system?
- It gets inside your system along with the installation of any new software applications which the user does without thoroughly reading license agreements or reading without terms and condition. Most of these cases are sharing files like music, photos and many more in networking environment, visiting various adult websites are also liable behind the insertion of this threat inside your system.
- Attachments send via emails or Facebook, Skype messages. This trap is genuinely old, however it is always getting enhanced. The most recent hit is to influence it to look an associate sent you that email and it will also incorporate what seem, by all accounts, to be business related documents inside. Make sure to search for the file attachment before you take a gander at the document name. If it closes with .exe or it is .exe file then it’s most likely an infection!
- Bundling: Through third-party installers by concealing itself in freeware installation. It comes bundled with free application hosted from unreliable site. When user install those free application then this infection also gets installed automatically.
- It can also get attached with on your PC, if you frequently visit unsafe site like Porn sites or betting sites which contain illegal stuff. In addition, user should also avoid clicking on misleading ads and random links which redirects the victim to social media site.
- Spam emails: This browser hijacker gets into your computer through malicious email attachments in the spam emails tab. malicious infected attachments and download links in an unknown email.
- Carelessness-It gets installed when you click unintentionally on any infected link. Always pay attention while clicking on unsafe links or hidden links.
- Torrents & P2P File Sharing: Online Ads are another common culprit. Torrent sites especially are well known for their tricks involving multiple fake download buttons. If you click on the wrong button you’ll get a file to download that is named exactly like the file you want. Unfortunately what’s inside is actually the virus.
- Fake download websites are another wellspring of this programs. These sites have worked in calculations, which enable them to duplicate your search queries and influence the search engines to trust they have an ideal match for your search. When you endeavor to download a file from such a webpage the name will fit, but the file that you have downloaded are really going to be loaded with infections, viruses, malware and other threats. So it is never a smart thought to open documents got from arbitrary sources without scanning them for infections first. Always keep an anti-virus program on your machine.
Also Read: What is Losers Ransomware? Guide to Remove from your PC?
Tips to Prevent HydraCrypt Ransomware from Infecting Your System:
1. Enable your popup blocker: Pop-ups and ads in the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs. So, avoid clicking uncertain sites, software offers, pop-ups etc.
2. Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update. By doing this you can keep your device free from virus. According to the survey, outdated/older versions of Windows operating system are an easy target.
3. Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
4. Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection. Thus always backup important files regularly on a cloud drive or an external hard drive.
5. Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like McAfee or a good Malware Removal Tool like Download Free Virus RemovalTool
6. Install a powerful ad- blocker for Chrome, Mozilla,and IE.
