What Is Locky Ransomware?
Locky is the name of a Ransomware that has been making its presence felt since Feb 2016 in the cyber world. Email & Social Engineering are the best used propagation medium for this ransomware to spread. Most emails with malicious documents attached, featured the popular ransomware strains of Locky.
If you want to safeguard your system from any kind of malware or virus in future then Download All in one Free Malware Removal Tool.
This ransomware surfaced in limelight when in February 2016, in the Hollywood Presbyterian Medical Center, paid a $17,000 Bitcoin ransom for the decryption key for their patient data. Locky infected the Hospital’s data through an email attachment disguised as a Microsoft Word invoice.
Distribution Methods:
Many diverse delivery methods for Locky have been used since the ransomware was released. These distribution methods include exploit kits, Word and Excel attachments with malicious macros, DOCM attachments, and zipped JS (Java script) Attachments. Locky ransomware widely infects through spam emails campaigns run by the attackers. These spam emails have mostly .doc files as attachments that contain scrambled text appearing to be macros.
How Locky sets up itself in the computer.
Once Locky enters your computer, it enables macro settings in the Word program, an executable file which is actually the ransomware downloaded on the PC. Thereafter, various files on the victim’s PC are encrypted by the ransomware giving them unique 16 letters – digit combination names with. shit, .thor, .locky, .zepto or .odin file extensions. Most of the files are encrypted using the RSA-2048 and AES-1024 algorithms and require a private key stored on the remote servers controlled by the cyber criminals for decryption. Once the files are encrypted, Locky generates an additional .txt and _HELP_instructions.html file in each folder containing the encrypted files. This text file contains a message (as shown below) that informs users of the encryption.
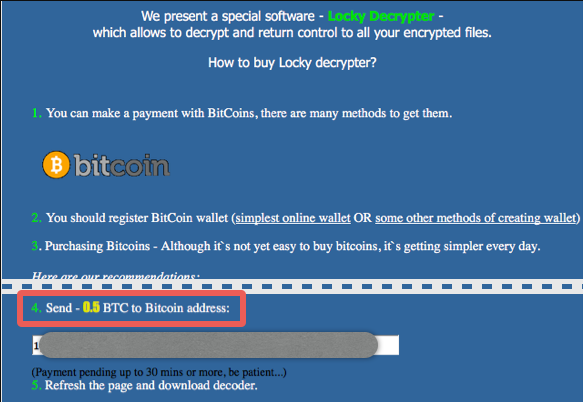
It shows a warning message that says files can only be decrypted using a decryptor developed by cyber criminals and costing 5 Bitcoins. Thus, to get the files back, the victim is asked to install the Tor browser and follow a link provided in the text files/wallpaper. The website contains instructions to make the payment. There is no guarantee that even after making the payment victim files will be decrypted. However, to protect its ‘reputation’ ransomware authors usually stick to their part of the bargain.
Targeted Browsers
- Google Chrome
- Mozilla Firefox
- Internet Explorer
Tips to Prevent Locky Ransomware From Infecting Your System:
- Enable your popup blocker: Pop-ups and ads in the websites are the most adoptable tactic used by cyber criminals or developers with the core intention to spread malicious programs. So, avoid clicking uncertain sites, software offers, pop-ups etc.
- Keep your Windows Updated:To avoid such infections, we recommend that you should always keep your system updated through automatic windows update. By doing this you can keep your device free from virus. According to survey, outdated/older versions of windows operating system are an easy target.
- Third party installation:Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Back up: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection. Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like McAfee or a good Malware Removal Tool like Free Malware RemovalTool. Apart from this we would suggest a regular updating of these software to detect and avoid latest infections.
- Do not blindly open mail in the ‘Spam’ or ‘Junk’ email sections. This could trick you into opening up an email containing the malware. Think before clicking on web links on websites or emails or downloading email attachments from senders that you don’t know. Do not click or open such attachments:
- Files with .LNK extension
- Files with.wsf extension
- Files with double dot extension (for example, profile-p29d..wsf).
- Disable the loading of Macros in Office programs. Opening an infected Word document file could prove risky!
