What is Nemesis?
Nemesis is a ransomware infection found by Michael Gillespie. Once in the system, Nemesis encrypts documents and affixes filenames with the ".id-casualty's ID_ [TOR site URL].63vc4" extension.
(for example, "test1.jpg" may be renamed to "test1.jpgid-12574_[qg89m5wo7h3id54ym.onion.to].63vc4").
Screenshot of files encrypted by Nemesis (".63vc4" extension):

More up to date variations of this ransomware utilize .aax55, .l454t, .id_[victim's ID]_[pizdoglaz@asia.com].t5019 .id_[victim's ID]_[webmafia@asia.com].t5019, or .id_[victim'sID]_[Blacklagoon@aolonline.top].nemesis extension for encrypted documents. Following effective encryption, Nemesis makes a HTML document ("### DECRYPT MY FILES ###.html"), leaving it in each encrypted folder, and after that changes the desktop background.
Screenshot of a ransom note ("### DECRYPT MY FILES ###.html") demanding the victims to pay the ransom to get their decryption key:
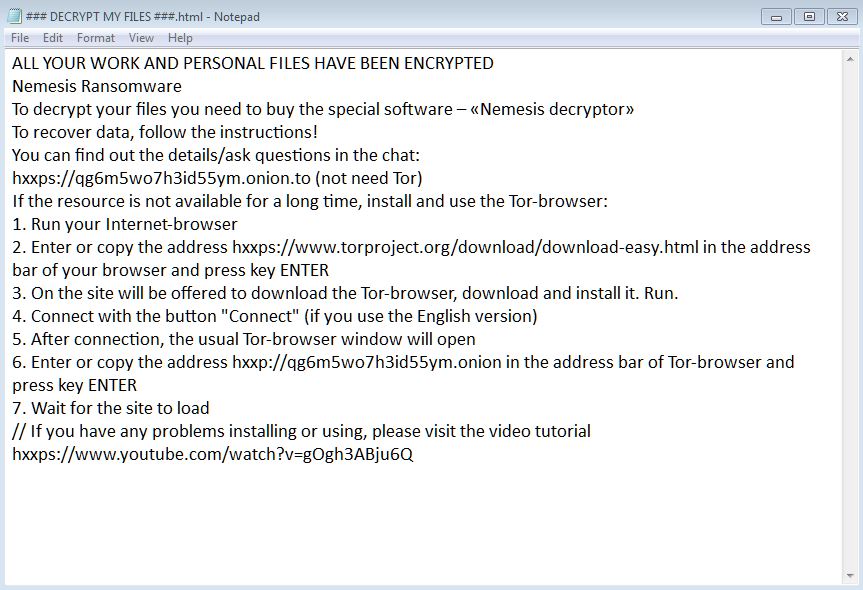
Screenshot of Nemesis ransomware Tor website (Live Support page):
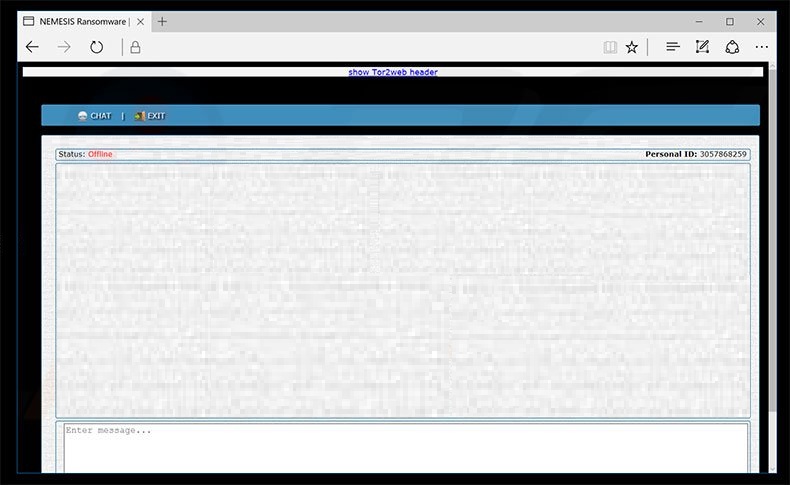
Screenshot of Nemesis ransomware desktop wallpaper:
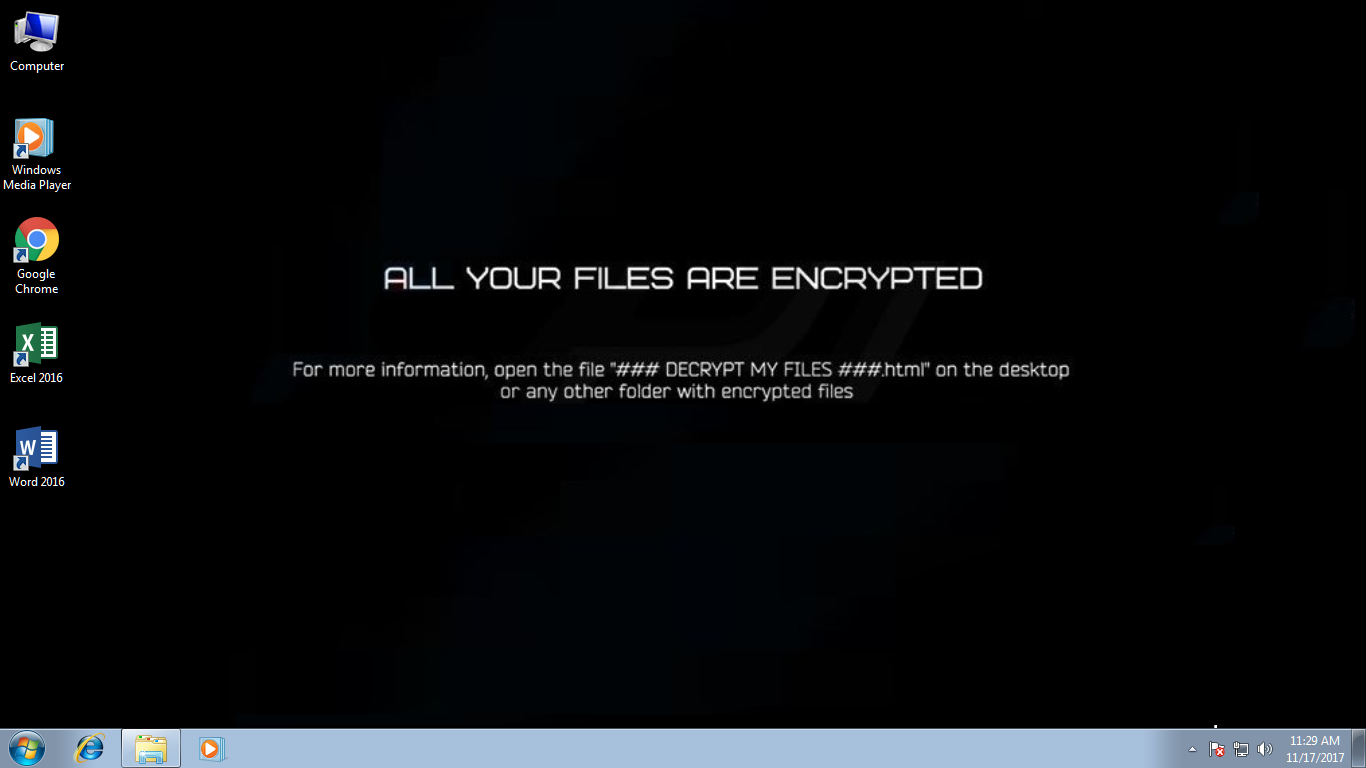
The HTML file contains message educating casualties of the encryption and demanding them to buy a decoding tool (by visiting a Tor site and paying a ransom). The cost, for now, is unverified, but the developers demand somewhere between $500 and 1500 in Bitcoins. At present, it is difficult to say whether Nemesis utilizes symmetric or topsy-turvy cryptography, however, breaking the encryption without the unique key is impossible. This key is put away on a remote server controlled by hackers themselves and victims are urged to pay off the ransom to get it.
So, what if your system is affected? What would you do next?
By any chance, if you believe that your computer could be infected with this infection, do not hesitate to eliminate Nemesis ransomware. This is the most straightforward approach to end its movement on your operating system. If you let this malware remain on your PC, this ransomware can cause significantly more harm by encoding another bit of your documents. Since quite possibly this infection is back online, we highly recommend you to run a full system scan with free malware removal tool.
Also Read: Cryptomix Ransomware Removal
Thinking of paying the ransom? Stop thinking, it’s a big “NO”.
Despite the fact that we highly suggest not paying the ransom, we understand that a few organizations would not have the capacity to get away without the information that has been put away on the encrypted PCs, so unfortunately in such cases, paying the ransom will be the only option to advance the business. Also, we can just advice you to not pay the amount. Remember that you can never be sure whether the criminals would give you a working decryption key.
These lawbreakers should never be trusted. Research demonstrates that they frequently disregard victims, once installments are made. There is a high possibility that paying won't convey any positive outcome and you will be scammed.
Things you must know about a ransomware attack
There have been incidents showing the users were hit by the same ransomware for the second time, even though they have already paid the ransom. From here, all that we can say is if you don’t act quickly and the right way, you might not get a second chance.
From here, we can just advise you to ignore all their demand and do not contact these criminals or pay any ransom. In doing so, you will ultimately support their criminal ventures. Unfortunately, there is no tool capable of restoring files encrypted by Nemesis ransomware. Therefore, the only solution is to restore files/system from a backup after eliminating the ransomware from the system.
Now, you need to follow the steps given to disable the ransomware initially and the eliminate it permanently by building a robust firewall all by yourself.
Temporarily Disable Nemesis ransomware in Safe Mode with Command Prompt
Step – 1 (enter safe mode)
- Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shutdown, then restart.
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next and followed by yes.
After temporarily disabling the ransomware, we need to create a strong firewall to fight against such intrusions and prevent them in future.
Tips to Prevent Nemesis ransomware from Infecting Your System:
1. Enable your popup blocker: Pop-ups and ads in the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs. So, avoid clicking uncertain sites, software offers, pop-ups etc.
2. Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update. By doing this you can keep your device free from virus. According to the survey, outdated/older versions of Windows operating system are an easy target.
3. Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
4. Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection. Thus always backup important files regularly on a cloud drive or an external hard drive.
5. Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like McAfee or a good Malware Removal Tool like Download Free Virus Removal Tool
6. Install a powerful ad- blocker for Chrome, Mozilla, and IE.
