Rakhni Trojan: It Encrypts and It Mines!
Ransomware making way for crypto-miners, a rising threat from the malware family and also ranked top among the online threats.
Moving with the trend, Rakhni Trojan ransomware which we have known since 2013 adds cryptocurrency algorithm to its armory.
What’s attention-grabbing is that the malware loader is able to choose which component to install depending on the device.
Our team at HTRI dug deep into the malware to figure out how the updated version works and where the actual threat lies.
Our researchers spotted Rakhni Trojan ransomware in Kazakhstan, Russia, India, US, Ukraine, and Germany.
The primary source of its distribution is through spam emails using malicious attachments.
The experiment carried by the team revealed that the malware is specifically targeting “corporate clients,” as the spam mail received by the clients was disguised as a financial document.
The spam attachment contains a PDF document presented as a DOCX.
Here’s where the actual trick is played! If a user tries to open the PDF file and allows editing, the system instantly requests permission to execute the file coming from an unknown publisher.
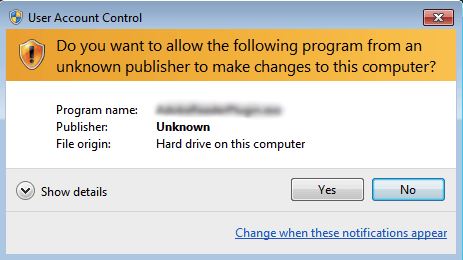
Rakhni shifts gears quickly after the user’s permission.
Operation hush-hush!
At first, the PDF file fronts as a document viewer. When the user tries to open it, instead of opening an error message pops up explaining why it didn’t open.
Consequently, as a result, it disables Windows Defender installing imitated digital certificates. After confirming that the ground is clear it makes a move and decides what to do with the infected device — demand a ransom by encrypting files or install a miner for cryptocurrency mining.
If company employees have shared access to the Users folder on their devices, the malware copies itself onto them.
Decisively, the malware spreads into the local network to infect every system in contact.
Example: if the malware manages to infect a system of an organization then it has the ability to spread through the complete network of that organization.
How does the malware decide whether to mine or encrypt?

The determination rule is straightforward: If the malware finds an administration folder called Bitcoin on the casualty's PC, it runs a bit of ransomware that encrypts files (PDFs, Office docs, backups, and pictures) and makes a demand for ransom within three days. Details of the ransom, including how much the cybercriminals benevolently guarantee to send by email.
In case there are no folders related to Bitcoin on the device, and the malware trusts it has enough capacity to deal with digital currency mining, it downloads a crypto miner that secretly produces Dashcoin, Monero or Monero Original tokens out of sight.
Stay safe! Don’t end up being a victim.
To abstain from getting infected by Rakhni and having actual damage imposed on your organization, be highly cautious about incoming messages, particularly you have received from new email addresses.
In case you're in any uncertainty, whatsoever, about whether to open an attachment, don't!
Additionally, pay complete attention to working OS warnings: Do not get into application coming from unknown publishers, particularly if the name sounds familiar to a famous program.
In the battle against miners and encrypters you won't turn out badly by taking these precautions:
- Train your data security staff and frequently check their awareness. If you require help related to malware stay connected with us and follow our articles regularly.
- Create backups of everything on your system and store it on a portable hard drive.
- Use dependable security software that works on regular updates; we recommend a program “Free malware removal tool.”
- Regularly test your corporate system for irregularities.
Even if you think your system is protected from such threats and that you would never have any trouble related to it, that’s no reason to leave your data to the malware developers. We have a free solution for you — the “Free Malware Removal Tool” — this tool works on the live malware updates which mean it is designed to detect and eliminate anything that stands a threat to your system.
Are you worried about your PC health?
Check your PC Health for Free!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
