Crypt0r Ransomware: A File Encryption Threat On Windows
Crypt0r Ransomware is a data encryption malware that compromises all Windows-based computers. It claims to provide an input key to get your system back but infiltrates the system with Crypt0r files virus.
The ransomware modifies the structure of the data on the local disks of Windows OS without informing users. Typically, hides and interfere in the functioning of other applications in your computer without letting you know.
Every ransomware weaponizes the encryption technique with which cybercriminals manipulate the security vulnerabilities of the computer and spreads a nasty infection to extort the users for money.
Crypt0r Ransomware: File Encryption Methods
Cybersecurity experts say that it deploys a full-fledged attack while targeting files such as video, audio, music, text files, web formats, databases, configuration files, etc.
“Instead of directly locking files, the Crypt0r Ransomware changes the filenames completely by adding a random combination of 8 characters as an extension to the files. For example, .qqjuBOaf, .2lwnPp2B, or .aqhATfjK are some Crypt0r files virus extensions.”
Though Crypt0r Ransomware infected people are presently low at the moment, but security researchers are yet to obtain a legitimate ransom note belonging to this file-encryption threat.
Therefore, there is not much to say about the threat but it posses all the necessary properties to encrypt a large number of files. Being the new strain of the infamous WannaCry and NotPetya ransomware viruses, Crypt0r encrypts files and scrambles the name of the files.
This let the attackers behind the ransomware obscure the contents of the computer such that users couldn’t recognize it nor could use it. We never advise victims of the Crypt0r Ransomware to agree and cooperate with the criminals behind this project.
Unfortunately, it is difficult to obtain keys to decrypt crypt0r files virus. After entering into your system, the ransomware impacts your computer and victims are forced to contact cybercrooks at decrypt0r-help@protonmail.com email address.
Even if the victim contacts the developer and pays the ransom, it is hard to crack Crypt0r ransomware AES/RSA cipher encryption algorithms. It is recommended that you should never believe such cybercriminals because they hide the keys on servers and blackmail users for keys release.
Thus, it is important to use a successful robust anti-malware removal tool such as Malware Crusher to prevent crypt0r virus files entry into your computer.

Crypt0r Ransomware Impacts Your System
It quickly spreads through spam emails, websites, peer to peer file sharing, freeware (fake software updates), cracked or pirated software and social hijacking. It degrades the computer performance and compels you to pay money for your own files within some time limit.
Once victimized, the ransomware attacks your system, web browsers settings and corrupts hard drive of the computer. Applications do not respond properly and sometimes applications lack few important program files.
Once it is inside your computer, the .qqjuBOaf file extension or .aqhATfjK file extension virus scans your hard drive to detect all such files that can be locked. It targets personal files, system operating files and other manually downloaded or saved files.
To lock files, the ransomware will employ strong cryptographic techniques and try to change the structure of your files. In short, the file encryption process is strong and is often impossible to 'crack'.
After the encryption, Crypt0r ransomware automatically generates a ransom note and display it on your desktop in a file named _HELP.txt.
Cybercriminals via these threats steal information like IP address, URL’s Search, browser history, search queries, username, ID, passwords, banking information and ATM Card information.
Crypt0r Ransomware is detected as following by the antiviruses:
- Gen:Heur.Ransom.Imps.1 (B)
- Ransom.Gen!8.DE83 (CLOUD)
- Malware@#2flwppvkgy64d
- RDN/Generic.hra
- Trojan-Ransom.Win32.Gen.kxn
- Win.Trojan.Agent-6807435-0
- Trojan.Encoder.26980
- W32/Gen.FEE!tr.ransom
- Win32.Trojan.Gen.Pegl
- malicious.3007cd
Temporarily Disable Crypt0r Ransomware in safe mode using Command Prompt
If you can’t access your computer, then it might become impossible to remove Tfude ransomware. However, system reboot in Safe Mode could give you entry into your computer followed by creating a system restore point.
Once you are into your computer, perform a full system scan using the antimalware tool which we have suggested at the end of this article.
Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shut down, then restart.
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
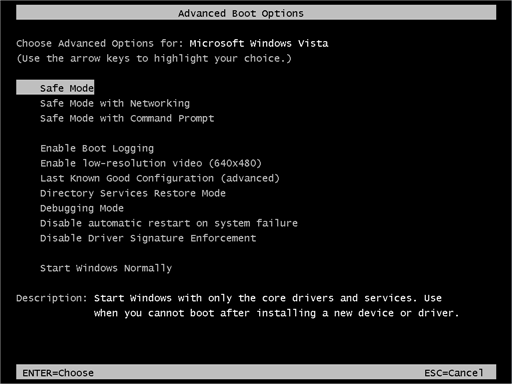
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click Restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
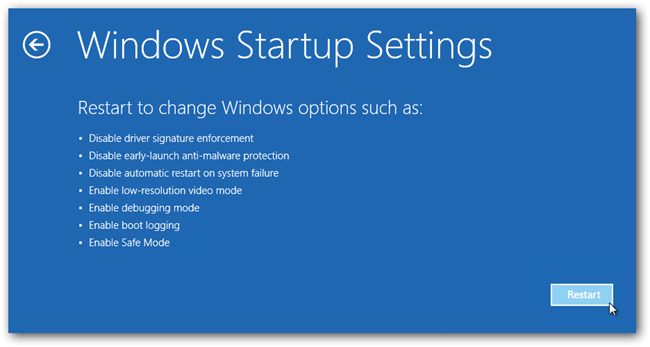
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Restore System
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
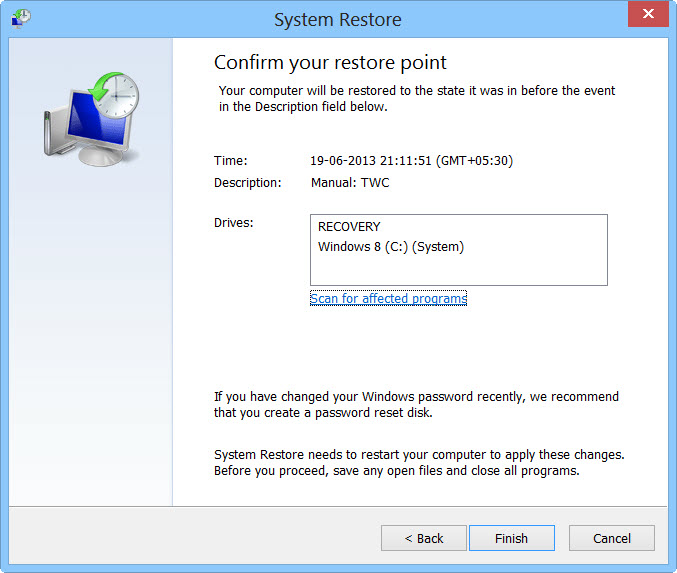
- Then, click next and followed by yes.

At present, your computer is in a state that has its file and data backed up at a safe restore point. We also suggest you to make a copy of your backed up data into some external hard drive.
It is now time, to reinstall your Windows via an external source such as USB drives, CD or DVD and portable HDD devices.
While installing Windows, allocate disk space to C, D and E drive. If asked to restore any files, select the restore point and get the backed up data into the new operating system.
Your system format is complete, also your data is backed up. Now you must create a strong firewall against such malicious threats to prevent the future attacks.
Cyber attackers are very advanced and had learned to gain illegal access to the computer. More than that, they make their malware more adaptable, resilient and damaging. It is impossible to stop cyberwarfare and cyberterrorism by common antivirus software.
Thus, the best preventive step is to upgrade our cyber defense systems at home and office computers with those cybersecurity tools that provide real-time protection feature, quarantine feature, web protection and anti-exploit technology.
If your computer doesn’t have such security software, then download ITL Total Security and Malware Crusher to prevent ransomware attacks on your system. Both are reputable, vigilant and robust in creating a shield 24X7 against any cyberthreat.
These tools are highly recommended if you are willing to give advanced security to your PC. Their 5-minute function could be a savior for your computer!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
