.Good Ransomware - Money Scandal
Ransomware is cryptovirology (extortion-based security) threats that block access to your computer unless a ransom is paid. The .Good Ransomware is an open ransomware project called as Hidden Tear.
The Ransomware encrypts a range of files mostly in use by the users and blocks access to them by infecting the whole computer. The malware changes the extensions of the affected files to .Good, making impossible for the users to open them without decryption technique.
The Hidden Tear’s .Good Ransomware uses an AES encryption algorithm to lock the access to the files.
Whenever you access affected file, a warning error message displays which we call a ransom note.
After encryption, all desired files get locked computer's performance slows down. The key purpose of this ransomware is to block the user data, to steal it and demands for money in exchange for decryption.
Encryption and decryption technique works in favor of cyber attackers because by blocking user access in their own computer, they force users to pay for their files.
.Good Ransomware - An Evident Sneaky Threat
This ransomware is extremely stealthy and most of the user’s don’t realize that their computer is infected until their all data is inaccessible. The ransom note generates when the virus insidiously activates inside the files to block the user.
Now, if you are in some similar situation, then you need to know something significant to prevent your computer from this cryptovirology threats.
Paying ransom is not really a good option and won’t lead you to a good reaction because once you start paying a ransom, the cyber attackers will demand more.
The reason for that is the hackers might not send you the decryption codes (also called as decryptors or decryption tools). If you do not get the tool to unlock the files, your data will be locked up forever.
On accessing the locked file, a ransom note named HOW_TO_RECOVER_FILES.TXT open and suggests to contact attackers at the support mail: dsupport@airmail.cc. Additionally, demands money in BTC to unlock your files.

In such cases, you should immediately install a combating antimalware tool. For your ease, a malware removal tool is the best option as it helps you to delete all the unwanted ransomware files. Thus, prevention is better before the ransomware starts affecting your computer in severe ways.
Unfortunately, a ransomware attack implications are beyond the cost of the ransom and it could let you face;
- Cost of replacing compromised devices
- Loss of proprietary data
- System downtime, which affects the ability to operate
- Reputational damage
- Potential legal penalties arising from poor security or handling of data
Impacts Of .Good Ransomware
This ransomware easily spreads through spam emails, websites, peer to peer file sharing, freeware, cracked or pirated software, and social hijacking. It degrades the computer performance and compels you to pay money for your own files within some time limit.
Once victimized, the ransomware attacks your system and web browsers settings in the following ways;
- It consumes high CPU power and lowers down the overall performance of your computer.
- The computer boots up for no reason, freezes while you are working.
- Slow internet browsing speed might cause the internet to stop unexpectedly.
- Fake alert messages and notifications pop-ups to asking you to pay the ransom.
- It leads to irrelevant web search redirections and highly affects your web browsing experience.
- It steals your browsing information and personal data such as IP addresses, banking details, passwords and login credentials.
- It also changes your Windows Registry editors to remain undetected from anti-viruses and anti-malware.Automatic download of executable files from unknown sources and unsecured websites.
- Sending emails and maintaining your online presence on Social media though you aren’t logged in.
It is a big scam of cybercriminals! It offers to decrypt 3 files for free, however, their primary aim is to steal information like IP address, URL’s Search, browser history, search queries, username, ID, passwords, banking information and ATM Card information.
However, a robust anti-malware removal tool Malware Crusher is a self-protected firewall protection application that finds out all the ransomware and related cryptovirus files, uninstall them and delete them from the roots of system registry editors.

The one-click download button downloads the anti-malware tool and creates a strong firewall against all kinds of cyber threats. Additionally, protect your Windows-based computer automatically.
Why .Good Ransomware Creators Target Home Users
- Because home users don’t have data backups.
- Because of less cybersecurity education.
- Because of lack of awareness cyber attackers attacks home users by social engineering techniques.
- Home users don’t keep their software up to date.
- They fail to invest in cybersecurity solutions.
Affiliate schemes in ransomware help developers to earn profits each time whenever user pay a ransom. Ransomware use several evasion techniques that keeps itself hidden from the eyes of the victimized users.
The ability to remain dormant makes ransomware a very notorious malware with the features like fast flux, encrypted payloads and anti-sandboxing mechanism.
Automatic Preventive Method
You see a ransomware alert ransom note but cannot solve the issue by yourself. In such cases, you need an automatic scan of Malware Crusher a malware removal tool, to prevent ransomware from collecting your information and money.
Few of its malware removal capabilities are given below:
- It’s a real-time protection feature, performs a deep scan, detects malicious software, infected encrypted files within your system.
- The Quarantine feature of the tool removes all infected files from your computer in addition to keeping a record of all deleted malicious program.
- The tool detects, immobilize and delete all hidden keystroke logger software on your computer to prevent theft of your personal and sensitive information.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as anti-exploit technology and blocks .skype ransomware component before they hold files as a hostage.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities.
- It also acts as a Parental Control Tool to save your child from streaming wrong contents from illegal websites.
Rather than paying money, you must download Malware Crusher to fight against all components of ransomware. It automatically removes all the malicious threats including .skype ransomware and malware by fixing your computer in less than 5 minutes.
We also recommend you to establish a security awareness and be sure to update your system and software periodically. For this, you can follow our manual files removal guide.
Manual Files Removal Method
- Press Ctrl + Shift + ESC together to open Task Manager. Look for suspicious files, right click on it and click End Task.
- Now, open RUN box window by pressing Windows key + R . Type appwiz.cpl on it, this opens Programs and Features window.
- Select each suspicious program and uninstall it one by one. Once the uninstallation is complete, restart your computer and again redirect yourself to Programs and Features window to check whether the application is present or not.
- When convinced, press Windows key + R to open RUN box window. Type regedit on it, hit OK and then click Yes.
- Go through HKEY, HKLM, etc. files and find all suspicious files and delete them from Windows registry editors

- You can also delete malicious extensions from your browsers like Chrome and Firefox.
1. Click on the Customize and control menu icon at the top right corner of Google Chrome.
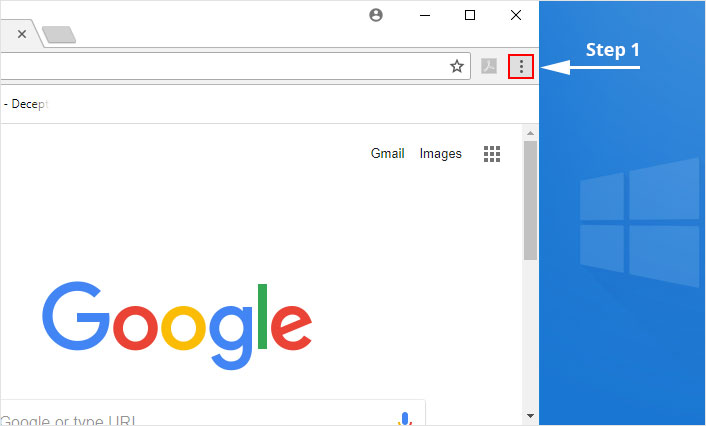
2. Select "More tools" from the menu.
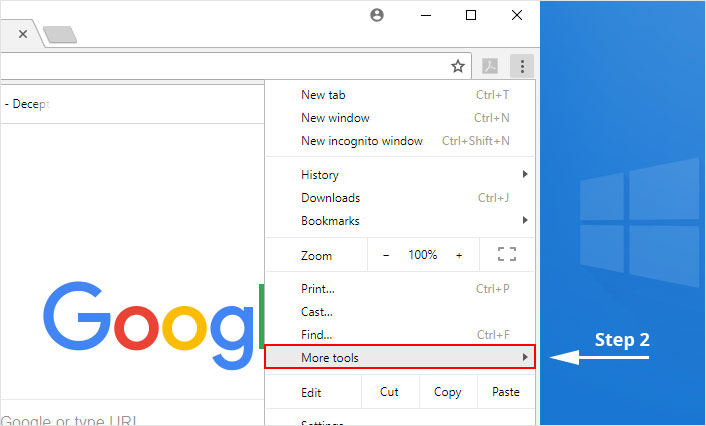
3. Select "Extensions" from the side menu.
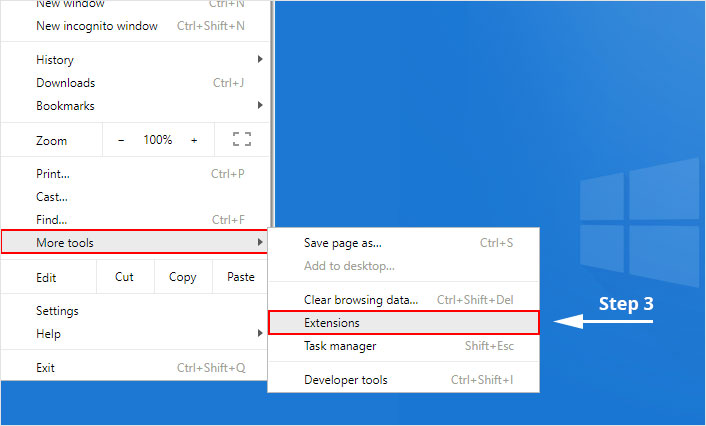
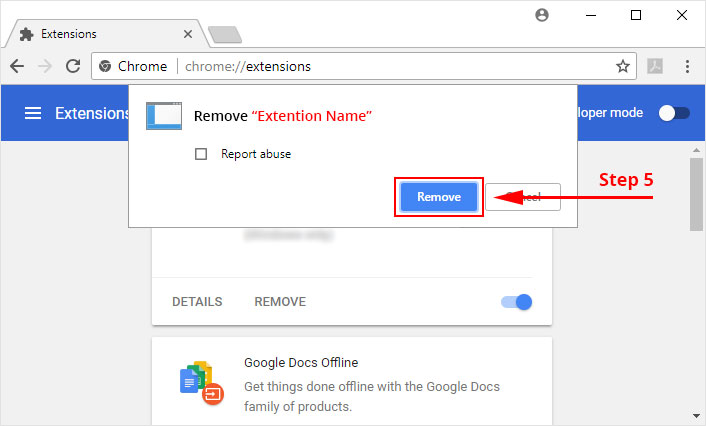
4. Click the remove button next to the extension you wish to remove.
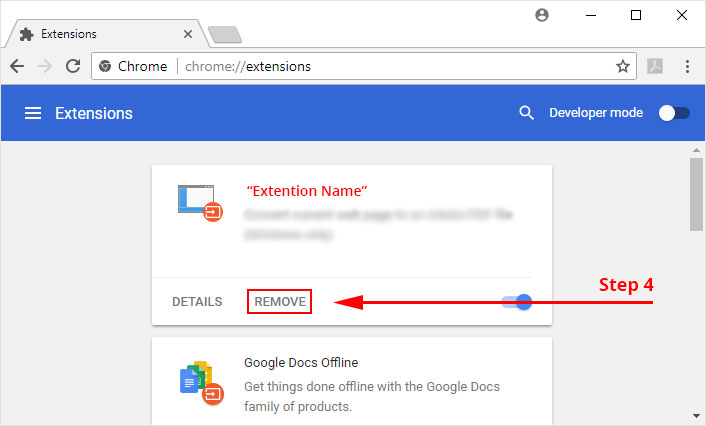
5. It will confirm again, click “remove” and the extension is finally out of the system.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
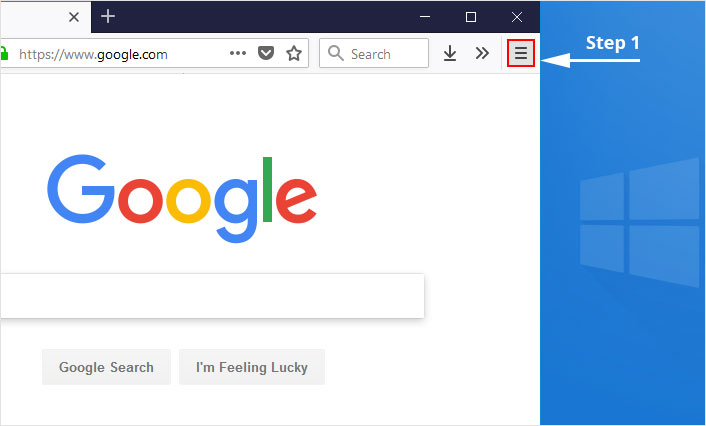
1. Click on the “menu” button at the top right corner.
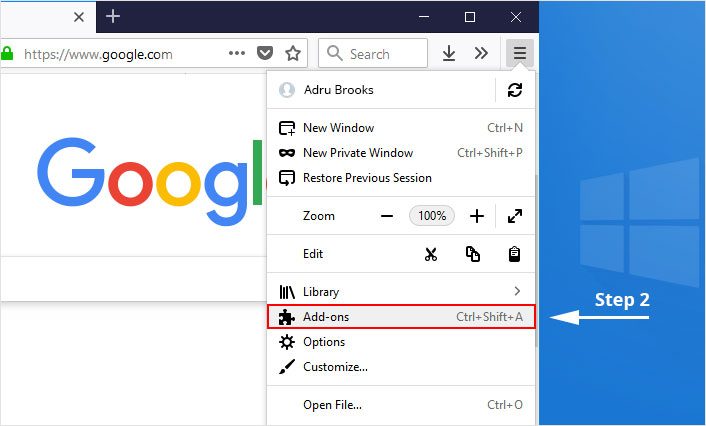
2. Select “Add-ons” from the menu.
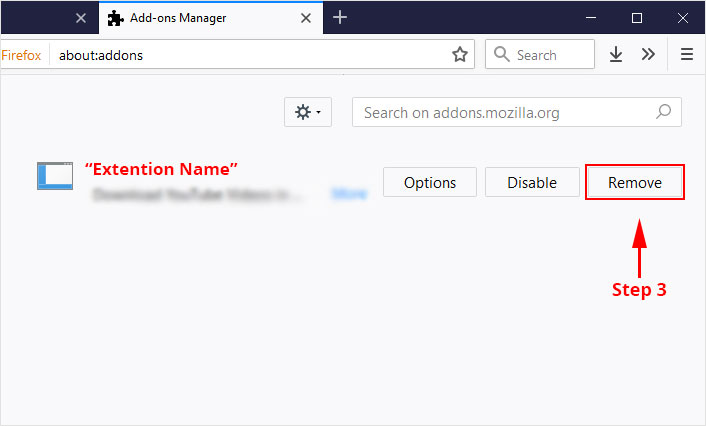
3. Click the “Remove” button next to the extension you wish to get rid of.
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
The manual method sometimes might not work at Windows OS because finding suspicious and modified registry files in registry editors is a difficult task. On the other hand, if a useful file deletes, then the windows stop working properly.
That’s why it is highly recommended to use an automatic tool to prevent and remove .Good ransomware attacks and infections on your computer. If you wish to get more news and awareness on the happenings of the cybersecurity, then keep visiting us.
To get a better security awareness on preventing cyber-attacks and internet security threats, keep visiting us and forget not to download Malware Crusher. Its 5-minute function could become a savior for your Windows computer.

Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
