.Promos Ransomware Threat Detection and Protection
Browsing the web is always entertaining, but it can become dangerous when a dreadful infection like ransomware or any other form of malware enters into your computer from a click on a high-risk site like gambling, torrent, porn, etc.
Though the internet looks secure, with the increase in cyber attacks, spam emails, malicious documents, etc. sometimes it is difficult to trust the web URL on the internet search engine.
Anonymous hackers somehow use various online techniques to leave malicious programs into your computer for impacting the operating system’s performance to a large extent.
One such unwanted program that should never exist in your computer is .Promos Ransomware, designed to encrypt data and files. In other words, it locks down your files, data, online information, etc without user consent.
The ransomware belongs to STOP/Djvu ransomware family. If your documents, music, photos, web pages, etc don’t open normally due to .promos file extension, then your machine is infected and center of cause is this newly found ransomware.
Once launched, it locks all the stored files on a computer, stop drives from functioning normally and blocks the networked drives. It is malicious software that hijacks a whole machine by locking files and other software.
What is Promos Ransomware?
.Promos ransomware is a file-encrypting malware that usually gets inside the system via malicious email and process data encryption. It is a new variant of the ransomware that appends .promos extension.
Like all other ransomware, it is also a file-encrypting malicious code that hijacks your computer to encrypt photographs, music records, business reports, pdf, docs and all other data only after utilizing file lock and encryption cipher techniques like AES/RSA.
To lock any file, the ransomware adds the .promos extension. For example, filename.jpg encrypts to filename.jpg.promos.
Typically, it spreads after it hacks into remote network computers and desktop services. It should also be noted that this dangerous ransomware encrypts mapped network drives, unmapped networks, host drives and shared virtual machines.
On clicking any locked file, a ransomware _readme.txt opens demanding $980 in bitcoin. Like every other note, the message tells users to pay ransom in bitcoins to get back the access to all the encrypted files.
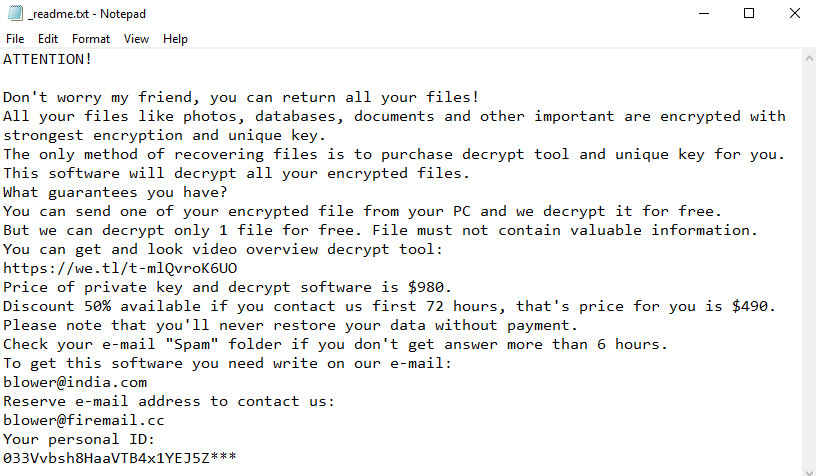
Eventually, once the payment is done the ransomware developers in the note claims to free your system unharmed. However, from the reports by cybersecurity expert, this claim was found misleading the victims of ransomware.
Typical of like ransomware, this claim is false and once the payment is done, the cyber attackers demand more money rather than leaving the system. We suggest you to never make payment and must find a way to delete .promos ransomware files.
How to decrypt Promos Ransomware?
It is nearly impossible to recover all the locked files as the encryption algorithm is strong and runs on private keys of malicious programmers. Therefore, as of now, it is quite notable that forging out any decryption key and tool is not realistic.
Moreover, to make any decryption tool it is important to reverse engineer the program code of ransomware’s encryption mechanism. Unfortunately, more time is required to break down the encryption mechanism.
As per security experts, presently .promos ransomware decryptor tool is not present and is yet to be developed. Since there is no decrypt tool to recover your files, we recommend taking some preventive measures.
NOTE: Do not belive cyberattackers that aks you to pay money for decryptor tool because .promos file recovery via this isn’t possible and you would lose your money too.
Here we would recommend you to install a robust antimalware tool named Malware Crusher by clicking the free download button.

How dangerous is Promos Ransomware in Your Computer?
- Alters your Windows-based computer files without your permission.
- Blocks some important applications like antiviruses, system settings, firewall settings and command prompt.
- This malware locks files of games, ppt, pdfs, docx,xlx and other files.
- Cyber attackers use names and logos of different trustworthy companies to make ransom note and make it believable to the users.
- It highly affects your web browsing experience and shows irrelevant search results.
- It tricks you into installing other malicious apps and malware which brings more problems.
- BSOD (Blue Screen of Death) errors in Windows.
- Keeps a record of your IP address, browser history and activities, passwords, bank account details, etc. in your system.
- Infect external media drivers.
Research shows that this ransomware virus makes your computer vulnerable to remote attacks and use the following techniques to inject ransomware into your computer.
It also posses some properties related to Cryptomix ransomware responsible for increasing botnets for cryptomining.
- Social Clickjacking
- Spam emails
- Torrents and P2P file sharing
- Bundling
- Freeware (fake software updates)
This let the attackers behind the ransomware obscure the contents of the computer such that users couldn’t recognize it nor could use it. We never advise victims of the .promos Files Virus to agree and cooperate with the criminals when they demand money.
Instead, we suggest victims to follow the below-mentioned ransomware removal guide that helps you to get back the access of your computer. Additionally, at the end of the article, you will get the chance to download a .Promos Ransomware Removal Tool for free.
Temporarily Disable .promos Ransomware in safe mode using Command Prompt
If you can’t access your computer, then it might become impossible to remove .Promos Ransomware Virus. However, system reboot in Safe Mode could give you entry into your computer followed by creating a system restore point.
Once you are into your computer, perform a full system scan using the antimalware tool which we have suggested at the end of this article.
Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shut down, then restart.
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
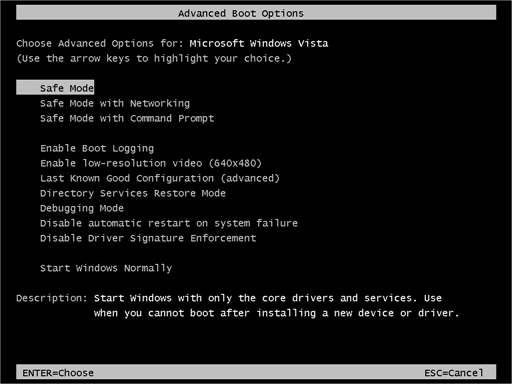
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click Restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
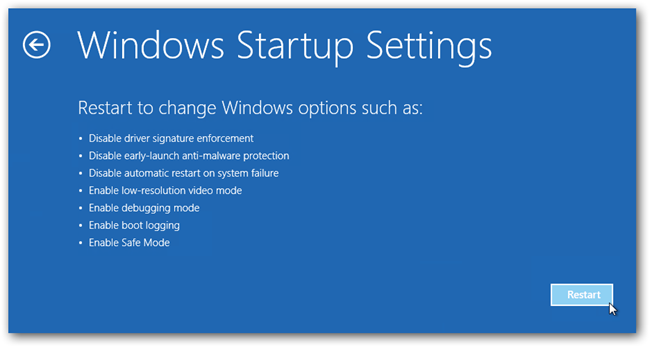
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Restore System
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
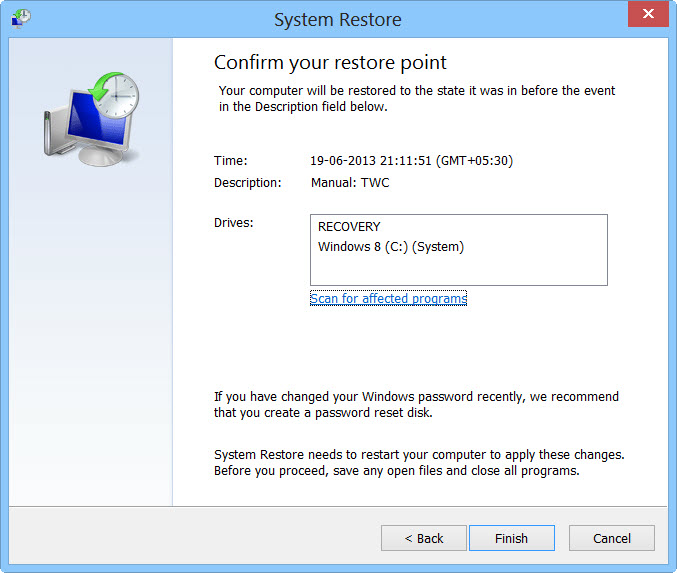
- Then, click next and followed by yes.
At present, your computer is in a state that has its file and data backed up at a safe restore point. We also suggest you make a copy of your backed up data into some external hard drive.
It is now time, to reinstall your Windows via an external source such as USB drives, CD or DVD and portable HDD devices.
While installing Windows, allocate disk space to C, D and E drive. If asked to restore any files, select the restore point and get the backed up data into the new operating system.
Your system format is complete, also your data is backed up. Now you must create a strong firewall against such malicious threats to prevent future attacks.
Cyber attackers are very advanced and had learned to gain illegal access to the computer. More than that, they make their malware more adaptable, resilient and damaging. It is impossible to stop cyberwarfare and cyberterrorism by common antivirus software.

Thus, the best preventive step is to upgrade our cyber defense systems at home and office computers with those cybersecurity tools that could delete .promos ransomware with their real-time protection feature, quarantine feature, web protection and anti-exploit technology.
Note: If your computer doesn’t have such security software, then download ITL Total Security and Malware Crusher to prevent malware attacks on your system. Both are reputable, vigilant and robust in creating a shield 24X7 against any cyberthreat.
These tools are highly recommended if you are willing to give advanced security to your PC. Their 5-minute function could be a savior for your computer!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
