Stopencrypt@qq.com Ransomware - A Rising Cyber Threat
The Internet Society unsealed a new variant of CrySis Ransomware behind the unauthorized change in Windows registries, slow internet speed and performance of computers at offices and homes.
The cybersecurity investigators dubbed the variant as Stopencrypt@qq.com Ransomware, currently attacking private organizations, hospitals, colleges, universities and statutory bodies of the government in the major cities of the world.
The research from security experts shows the ransomware as a cause of data loss, file loss and data theft. If your documents and files are encrypted with stopencrypt@qq.com extension, then your computer is probably under the cyber attack.
The in-depth investigation from experts has revealed answers to many questions and conclude this threat as a very powerful malicious program possessing different features of major threats like malware, viruses, scareware, keyloggers and hijackers.
What is [Stopencrypt@qq.com]].adobe Ransomware?
It belongs to the family of Dharma ransomware, takes control after crawling in your system and encrypts many useful files. After invasion and encryption, the stopencrypt@qq.com ransomware demands payment in bitcoins to decrypt the data.
Like all other ransomware, it is also a file-encrypting malicious code that hijacks your computer to encrypt photographs, music records, business reports, pdfs, docs and all other data only after utilizing file lock and encryption techniques like AES/RSA.
These techniques are the part of its malicious code that modifies your system registry files in order to secretly allocate themselves into the infected machine for locking out the data and files.

Why [Stopencrypt@qq.com].adobe Is Dangerous?
First thing first, ransomware today is the most widely used malicious program and acts as a threat within the computer. The CrySis’s [Stopencrypt@qq.com].adobe ransomware is highly infectious. Its program code is smart enough to automate itself everytime it infiltrate a new system.
It quickly spreads through spam emails, websites, peer to peer file sharing, freeware (fake software updates), cracked or pirated software and social hijacking. It degrades the computer performance and compels you to pay money for your files within some time limit.
Once victimized, the ransomware attacks your system, web browsers settings and corrupts hard drive of the computer. Applications do not respond sometimes and adequately lack few important program files.
Cybercriminals via these threats steal information like IP address, URL’s Search, browser history, search queries, username, ID, passwords, banking information and ATM Card information.
Direct contact with hackers on C2 servers let them steal sensitive and financial information. Furthermore, it acts as a spy agent to our computer from the side of cybercriminals.
Once [Stopencrypt@qq.com].adobe ransomware is tricked into a system, it checks the PC for data files and encrypts them. Being the latest file-encrypting malicious code security experts are also not very aware of the functioning and how to prevent its infections?
Moreover, there is no process of decryption available to counterfeit the impacts caused by the Stopencrypt@qq.com ransomware. Additionally, there exists no Stopencrypt@qq.com decryptor tool to stop file-encryption.
Stopencrypt@qq.com.adobe Ransomware - Tricks and Encryption
Stopencrypt@qq.com ransomware infect the system and drop many files extensions like .fsh, .ntl, .arch00, .lvl, .pkpass, .bc6, .bc7 etc.
Once the files are encrypted with the .[stopencrypt@qq.com].adobe extension, a ransom note named FILES ENCRYPTED.txt file is created in all those folders where the data has been encrypted.
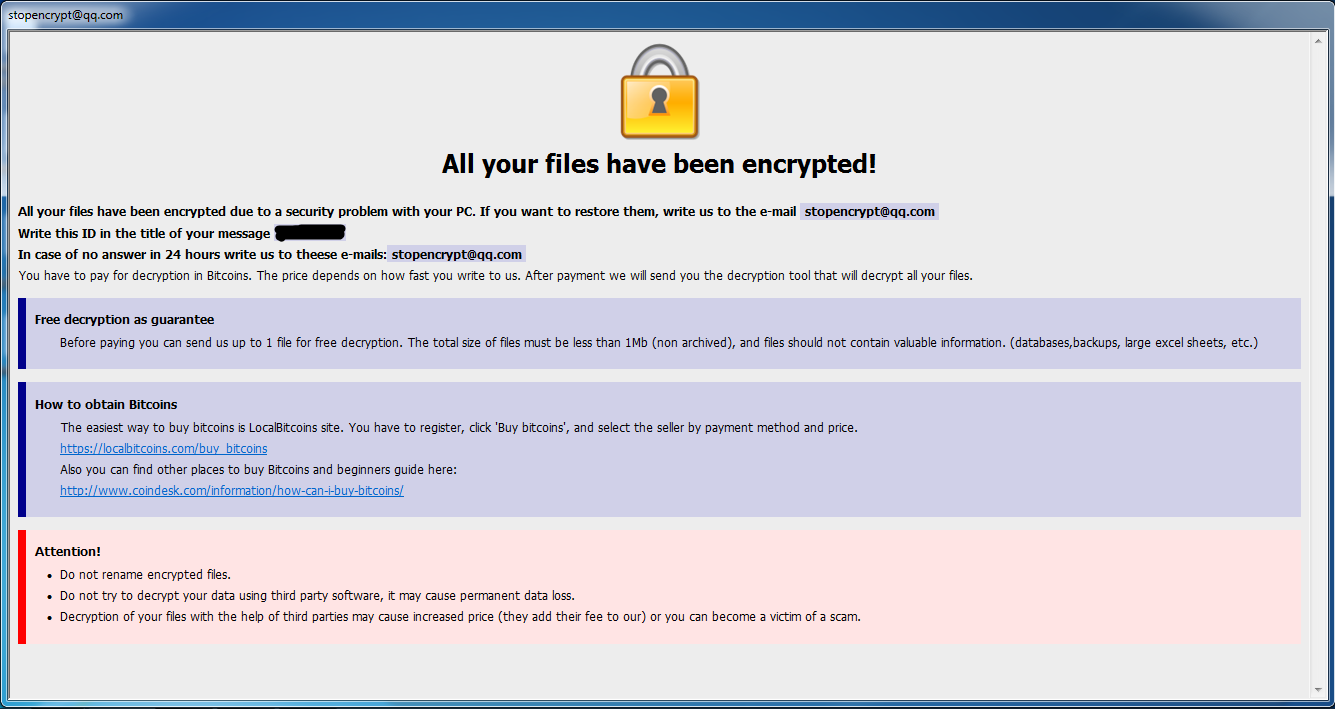
After dropping the ransom, cyberattackers demand payment in Bitcoins. The note randomly opens whenever the user tries to access an encrypted locked file.
It distributes via spam emails; the mail contains some infected attachment or link that on access enters ransomware. This threat targets all versions of Windows and for encrypting files, it uses RSA-2048 key (AES CBC 256-bit encryption algorithm), AES-265 and RSA encryption method.
The encrypted files are stored with random notes at %AppData% or %LocalAppData% folder. Important documents and files like .doc, .docx, .xls, .pdf etc are no longer working and can’t open.
The CrySis ransomware follows Symmetric/Asymmetric encryption algorithm to lock user’s access. Additionally, there are chances that it might work as a crypto mix variant to perform cryptojacking and coin-mining.
Analysis of Stopencrypt@qq.com Ransomware shows that it has become one of the most devastating cyber threats of 2018 and posses potential to become the next large-scale ransomware.
Are Stopencrypt@qq.com Ransomware Decrypt Tools Worth Using?
No, at this time it is impossible to recover all the encrypted files as the algorithm of encryption is strong and runs on private keys of C2 servers. Therefore, it is quite notable that forging out any decryption key and tool is not realistic.
Moreover, to make any decryption tool it is important to reverse engineer the program code of ransomware’s encryption mechanism. Unfortunately, more time is required to break down the AES/RSA mechanism.
As per security experts, presently it is impossible for researchers to reverse engineer the encryption process. If they succeed in doing that then protecting computers from CrySis, Dharma and Stopencrypt@qq.com Ransomware will be easy.

We also know that it is difficult to obtain keys to decrypt ransomware files. Even more, cyber attackers claim to generate keys and tools for your locked files. But, that would only happen if you pay them.
Paying ransom to the cyber attacker to get decryption tool is not a good option because the probability of getting cheat is more. Besides no attacker would like to offer you a solution to counterfeit the problem created by himself.
If you once pay them, doing so would encourage these bad guys in expanding their operations. We strongly, suggest you do not pay anything to the ransom and instead address the situation to internet law enforcement bodies of your respective countries.
At present, there exists no decrypt tool to recover your files, but it is important to take preventive measures before the ransomware starts attacking your Windows computer once again after entering into the advanced phase.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
