Experts have found a Linux version of the KillDisk ransomware, which is another addition to the KillDisk wiper malware family, previously used just to disrupt organizations by haphazardly erasing information and adjusting documents.
Seven days after experts at CyberX discovered features of a ransomware in the KillDisk variant, ESET discovered this ransomware and after testing its behavior it was found that this ransomware targets Linux systems.
Linux version messes the encryption key
As per the ESET analysts, the way this KillDisk ransomware version takes a shot at Windows and Linux is totally different, with the greatest issue being that on Linux, KillDisk doesn't save the encryption key anyplace on the system or on the web.
Generally, this would imply that victims could never have the capacity to decrypt documents since the encryption key would be lost promptly after the encryption procedure closes.
Fortunately, ESET scientists say they've revealed an imperfection in the Linux variation that allows them to regain the encrypted records. A similar deficiency does not exist in the Windows-targeted version of this ransomware.
ALSO READ: SAMSAM RANSOMWARE ATTACKS HOSPITALS, ICS FIRMS IN US
KillDisk ransomware, Windows version
The KillDisk ransomware variation that aims Windows operating system worked by encrypting every file by an AES-256 algorithm and afterward encrypting the AES keys with an open RSA-1028 key.
The private RSA key stored on the criminal's server allows them to decrypt the victim's files, but only after the victims paid a huge ransom of 222 Bitcoin (around $215,000). You can see the screenshot of the ransom note left behind in the Windows version below
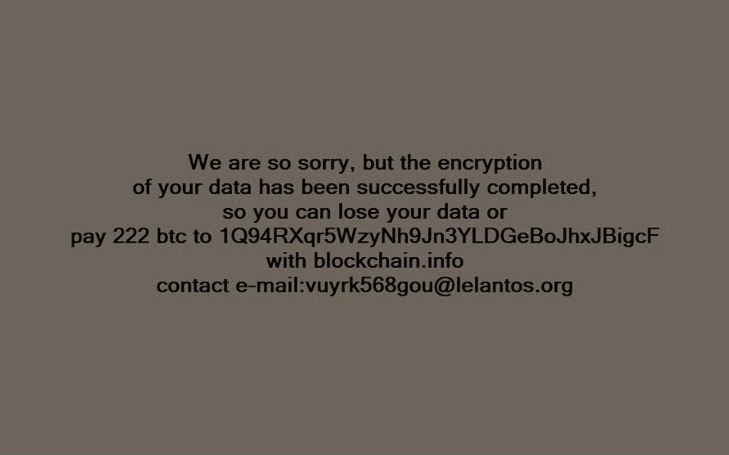
Criminals got the encryption keys on their servers by means of the Telegram protocol, utilized for the eponymous IM talk application. Along these lines, CyberX named the administrators of this ransomware crusade as the TeleBots gathering.
KillDisk ransomware, Linux version
The Linux variation spotted by ESET scientists earlier this week is altogether different from the Windows version.
Above all else, the Linux version does not converse with its Control and Command Centre by means of the Telegram API any longer. The encryption is additionally unique.
As demonstrated by specialists, the victim's "documents are corrupted employing Triple-DES connected to 4096-byte file blocks," and "every file is encrypted with a different kit of 64-bit encryption keys."
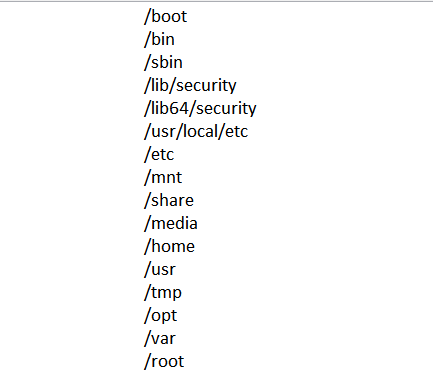
The Linux version targets these subsequent folders, at a depth of 17 subfolders, encrypting all files and adding the "DoN0t0uch7h!$CrYpteDfilE" extension.
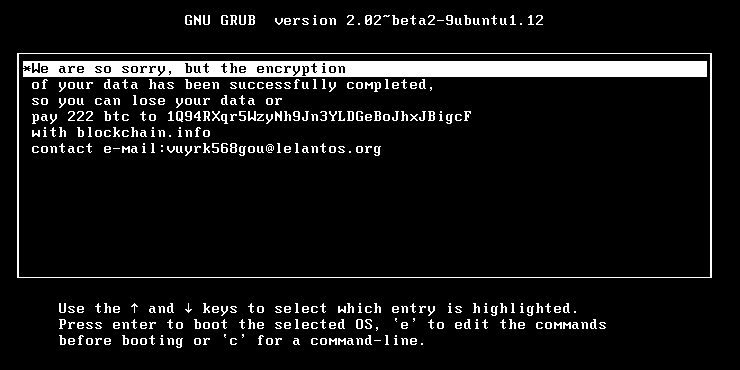
The KillDisk Linux ransomware will use the GRUB bootloader to display the ransom note by rewriting the user's boot sector.
The ransom note of the Linux version is an exact replica of the one shown in the Windows version, including the email address through which victims can reach out to the cybercriminals.
Before adapting the ransomware pattern, KillDisk had been used only in cyber-spying and cyber-obstruction operations.
Ransomware features used as a decoy?
In all assaults, Black Energy had utilized KillDisk to exterminate PCs and delete proof of their assaults, executed with other malware families.
The recently included ransomware highlights might be another approach to cover their assaults, with organizations supposing they may have been hit by ransomware, and not explore the gaps for other predictions.
The ransomware's immense payment request likewise plays in with this situation as it's crazy to assume that an organization may pay this much to recuperate their encrypted data.
The TeleBots gang may be hoping that companies would give up on their data, and this would skip all the possibilities of any other signs of the group's invasions.
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update. By doing this you can keep your device free from virus. According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection. Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like McAfee or a good Malware Removal Tool like Download Free Virus RemovalTool
- Enable your popup blocker: Install a powerful ad- blocker for Chrome, Mozilla, and IE.
