What is Paradise Ransomware?
The Paradise Ransomware has all the earmarks of being a “Ransomware as a Service” (RaaS). A RaaS is a place where ransomware designers create ransomware, deal with its improvement, and manage the Command and Control server in return for a little cut of all payoff installments made by casualties. The work of the offshoot, who gets whatever remains of the payoff installment, is to distribute the ransomware.
Also read: Guide To Remove X1881 Virus Easily
How does paradise ransomware infect a computer?
Right now, it is not known how Paradise taints a PC, but rather from sections in the event log of a contaminated PC, it might be through hacked Remote Desktop administrations. Once executed, however, Paradise will relaunch itself with a specific end goal to increase authoritative benefits and afterwards create a unique RSA-1024 key. This key is then used to scramble the greater part of the documents on each drive on the PC.
While encoding a document it will add the string as below:
“id-[affiliate_id].[affiliate_email].paradise to the record name. For instance, a document named test.jpg would be encoded test.jpgid-3VwVCmhU.[info@decrypt.ws].paradise.”
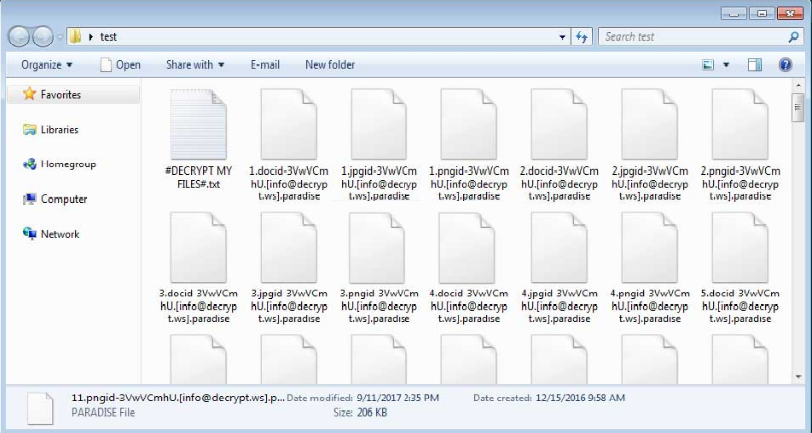
As Paradise ransomware utilizes RSA encryption to encode a document, the encryption procedure is moderate, which ideally permits the victim to distinguish the encryption occurring and stop it.
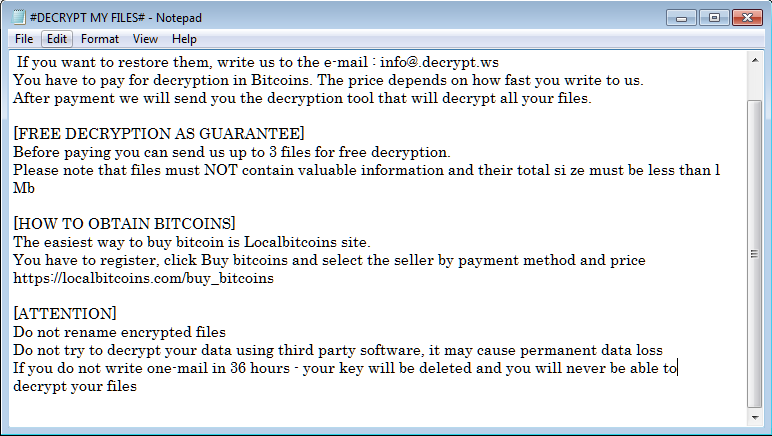
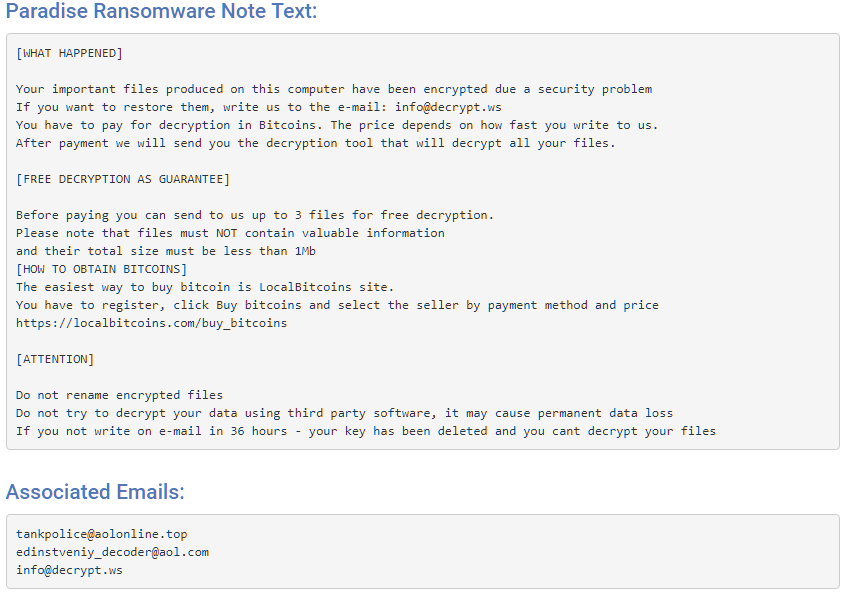
At this point when the ransomware has wrapped up a PC, it will drop some notes named #DECRYPT MY FILES#.txt in envelopes that a record was encoded. This payment note will contain the recipien’s email address and guidelines on the most proficient method to make the installment.
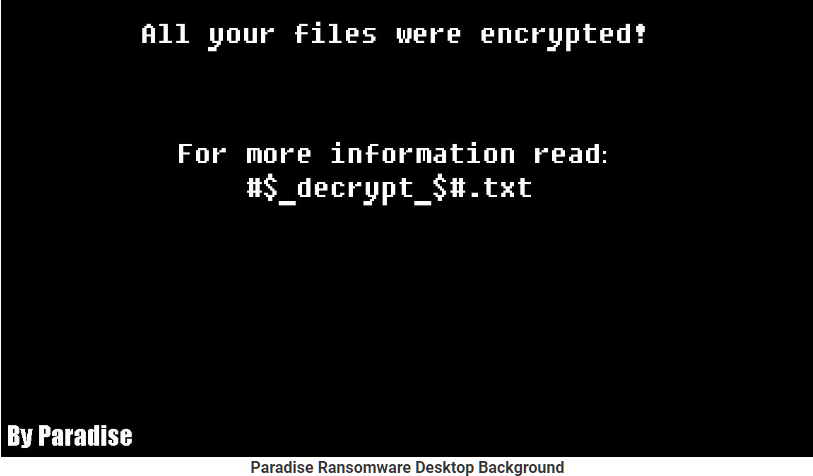
Paradise will then concentrate a base64 encoded backdrop picture and spare it to the %Temp% envelope as desk.bmp. The ransomware will then set this picture as a casualty's desktop foundation.
At last, the ransomware will compose the RSA encryption key that was utilized to scramble victim’s documents to the %UserProfile%\DecriptionInfo.auth record. This record will then be scrambled by an ace encryption that was packaged in the ransomware executable. This allows the ransomware designers to get hold of victim's unique RSA key after they have paid a ransom.
Temporarily disable Paradise Ransomware in Safe Mode with Command Prompt
Step - 1(enter safe mode)
- Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shutdown, then restart.
- While the computer is booting up at the very first screen start taping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next and followed by yes.
After disabling the firewall, we need to create a strong firewall to fight against such intrusions and prevent them in future.
Steps to be followed:
- Enable ad-blocker: Pop-ups and advertisements are the quickest and most reliable resources for the hackers to hijack the computer. So, enabling the ad-blocker would be a step towards blocking all the malicious websites or advertisements from popping up on the screen.
- Recommended Updates: Do not postpone any updates. If there is any recommendation from the computer to update the operating system, drivers or any security software you have do not delay it. Moreover, according to survey older version tend to be an easier target.
- Third-party installation: Avoid installing programs from untrusted websites because malware is bounded with such programs. If you still wish to install such program look for a trusted third-party website, read user review about the website before trying it.
- Frequent Back up: Make a habit of backing up all your personal data frequently as it assures the security of it, an attacker can crash your computer, wipe out all your personal data or might corrupt it so that the backup would be helpful in such emergency.
- Log out of all the websites once you are done using it, i.e., Banking websites, social websites. You could be leaving all your personal data vulnerable if you are using a public network.
- Make sure you are using a secure connection before viewing any website have a look for the padlock icon before the website URL.
- Use an authentic firewall, anti-malware, and Antivirus: It’s better to stay ahead, why wait for the malware to hit your computer. We recommend that you install an Antivirus like McAfee or a good Malware Removal Tool like Free Malware RemovalTool. Apart from this, we would suggest a regular updating of these software’s to detect and avoid latest infections.
