What is x1881?
Found by Malware Hunter Team, x1881 is another version of a well-recognized ransomware infection called CryptoMix. Once on the system, this malware encrypts all the documents and would lock all the information and rename the file extensions utilizing the "[32_random_letters_and_digits].x1881" design. For example, "sample.jpg" may be renamed to a filename, for example, "00A9531D13E7B26BC7E3A84F1414E6AB.x1881". Once the encryption is successful, x1881 leaves a text document with the ransom note in all the encrypted folders.
Ransom note:
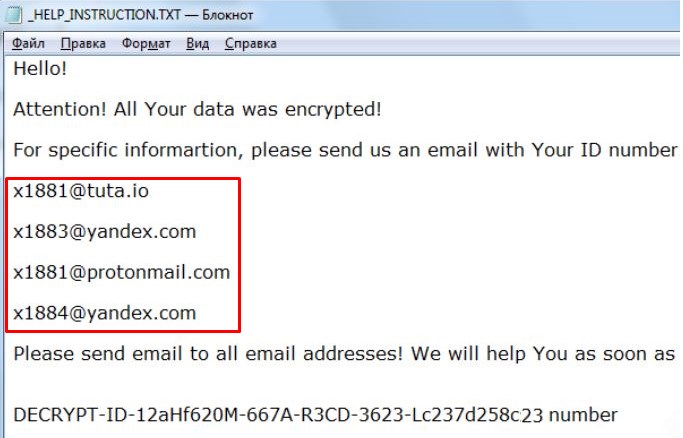
Also read: How To Remove Websrch.net Browser Redirect Virus
The folders that were encrypted will now have a new text document named "_HELP_INSTRUCTION.TXT." This new document contains a message demanding ransom from the victim for the decryption key and details on how to pay the ransom through cryptocurrency. At this point, the victims are already running on a deadline. If the ransom is not paid on time, the consequences can be harsh either the amount would be raised, or the user might lose his data. As per the latest update from the researchers, it is still unknown whether x1881 utilizes symmetric or Hilter kilter cryptography. In the two cases, decryption requires a decryption key of its kind. Cybercriminals store this key on a remote server and urge the victim to make the payment in the ultimate deadline, or the decryption key will be destroyed, and then no one would be able to retrieve their data. For now, there is no standard amount, designers of this type of ransomware infections ordinarily request something between $500 and $1500 in Bitcoins. No matter if the demanded amount is very less, never pay - As per the records a user once attacked has been under attack several times even after paying the ransom. There is a high possibility that you will be duped again- paying won't result in any positive outcome. Also, you will support digital offenders' organizations. Never endeavor to contact these individuals or pay any payoffs. Shockingly, at present, there is no program capable of decrypting x1881 ransomware, and the only way to retrieve your data is through the backup.
There are many ransomware infections equal to x1881. The rundown of cases incorporates (yet isn't constrained to) Blind, My Decryptor, Anubis, ZONEware, and Striked. In spite of the fact that, various cyber criminals create these infections, the end result is same- they encrypt and lock away information and make demands to release them. The main significant difference is the ransom amount that is to be paid and the kind of encryption algorithm utilized. Sadly, most utilize algorithm, (for example, RSA, AES, etc.) that create one of a kind decryption keys. Along these lines, unless the malware contains bugs/defects (for instance, stores the key locally) or isn't wholly created, reestablishing records physically (without the help an IT expert is not recommended) is nearly impossible. Therefore, x1881 and other such ransomware infections present a strong case for maintaining regular data backups.
Also read: How To Get Rid Of Winsnare Virus
How did x1881 ransomware infect your computer?
To distribute x1881 ransomware hackers usually utilize spam emails (irresistible attachments), third-party programs, third-party websites, freeware programs, freeware games, and trojans. Once opened, these malicious attachments (for instance, MS Office reports, JavaScript records, etc.) download and install malware. Unofficial software downloads, (for example, freeware download sites, free document facilitating sites, torrents, eMule, and so forth.) regularly introduce malicious executables as genuine programming. In doing such, these sources fool users into downloading and running malware. These malware's essentially open "entryways" for other malware to invade the system. These are the most widely recognized approaches to distribute ransomware.
Remove x1881 Ransomware in Safe Mode with Command Prompt
Step - 1(enter safe mode)
- Steps to be followed to enter the safe mode Win XP/Vista/7
- Click start, then shutdown, then restart.
- While the computer is booting up at the very first screen start taping F8 until you see the advanced boot options.
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Step – 2 (Restore system)
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
- Then, click next and followed by yes.
After disabling the firewall, we need to create a strong firewall to fight against such intrusions and prevent them in future.
Steps to be followed:
- Enable ad-blocker: Pop-ups and advertisements are the quickest and most reliable resources for the hackers to hijack the computer. So, enabling the ad-blocker would be a step towards blocking all the malicious websites or advertisements from popping up on the screen.
- Recommended Updates: Do not postpone any updates. If there is any recommendation from the computer to update the operating system, drivers or any security software you have do not delay it. Moreover, according to survey older version tend to be an easier target.
- Third-party installation: Avoid installing programs from untrusted websites because malware is bounded with such programs. If you still wish to install such program look for a trusted third-party website, read user review about the website before trying it.
- Frequent Back up: Make a habit of backing up all your personal data frequently as it assures the security of it, an attacker can crash your computer, wipe out all your personal data or might corrupt it so that the backup would be helpful in such emergency.
- Log out of all the websites once you are done using it, i.e., Banking websites, social websites. You could be leaving all your personal data vulnerable if you are using a public network.
- Make sure you are using a secure connection before viewing any website have a look for the padlock icon before the website URL.
- Use an authentic firewall, anti-malware, and Antivirus: It’s better to stay ahead, why wait for the malware to hit your computer. We recommend that you install an Antivirus like McAfee or a good Malware Removal Tool like Free Malware RemovalTool. Apart from this, we would suggest a regular updating of these software’s to detect and avoid latest infections.
