BlackHeart Ransomware Overview
BlackHeart AKA BlackRouter is a part of the Ransomware Family. This ransomware is bundled with the legitimate application ‘AnyDesk.’
This is a new ransomware and it’s recently captured by the security researcher. How this ransomware enters into the system is still unknown but we are assuming that when you visit a malicious website.
This ransomware appends the filename by adding. pay2me extension in the last.
Flow Chart
Visiting Malicious Website
↓
Bundled with Legitimate Application (AnyDesk)
↓
Drops 2 Files: AnyDesk.exe & BlackHeart.exe
↓
BlackHeart.exe encrypts the system and appends the filename by appending .pay2me extension at last.
Technical Analysis of Blackheart Ransomware
File Name: Blackheart.exe
MD5: 3E1F05B711BF194E17A5C55E6548D2C1
File Type: Executable
Detailed Analysis with Screenshot:
On execution of this ransomware, it initiates the encryption process by filtering its matching criteria of file extensions and folders that are going to be encrypted.
As shown below, this ransomware searches for these file extensions:
.txt .doc .docx .xls .xlsx .ppt .pptx .odt .jpg .png .csv .sql .mdb .sln .php .asp .aspx .html .xml .psd .rar .zip .mp3 .exe .PDF .rtf .CFU .mxl .epf .erf .vrp .grs .geo .elf .lgf .lgp .log .pff .mft .efd .ini .CFL .cer .backup .tiff .jpeg .accdb .sqlite .dbf .cdr .dwg .gif .mp4 .avi .mkv .wmv .webmp .bak
As shown below, this ransomware searches for these folders:
|
Program Data
|
|
Desktop
|
|
Download
|
|
Users
|
|
Documents
|
|
Pictures
|
|
Videos
|
|
Music
|
|
User Profile
|
|
All Users
|
|
Application Data
|
|
App Data
|
It also encrypts the data of other System Drives.
Once it is found and encrypts a file, it will append the .pay2me extension to the affected file.
Once it has accomplished the encryption process, then it deletes the Volume Shadow Copies from the system by initiating the CMD.exe that executes delete command (/c vssadmin.exe delete shadows /all /quiet)
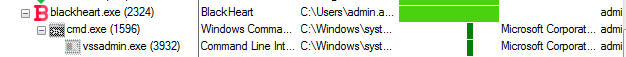
Figure 1 Process Tree
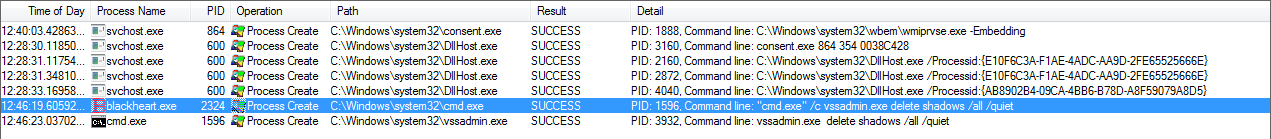
Figure 2 Deletion of Volume Shadow Copies
Once the encryption is accomplished along with the deletion process, then it drops 2 Ransom Notes on each drive of the system:
|
%Desktop%\ReadME-BLackHeart.txt
|
|
All Drives:\ ReadME-BLackHeart.txt
|
As shown below, the content of the ReadME-BLackHeart.txt:
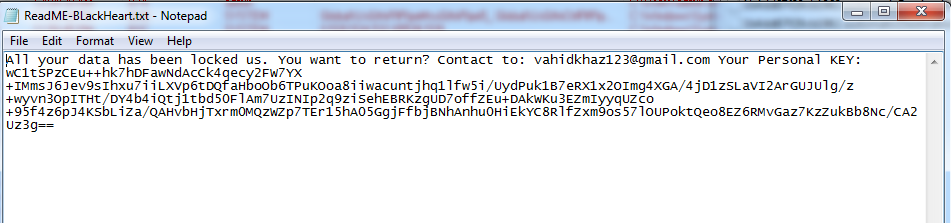
Figure 3 Ransom Note
At last, it shows the Ransom Note Message on the Screen:
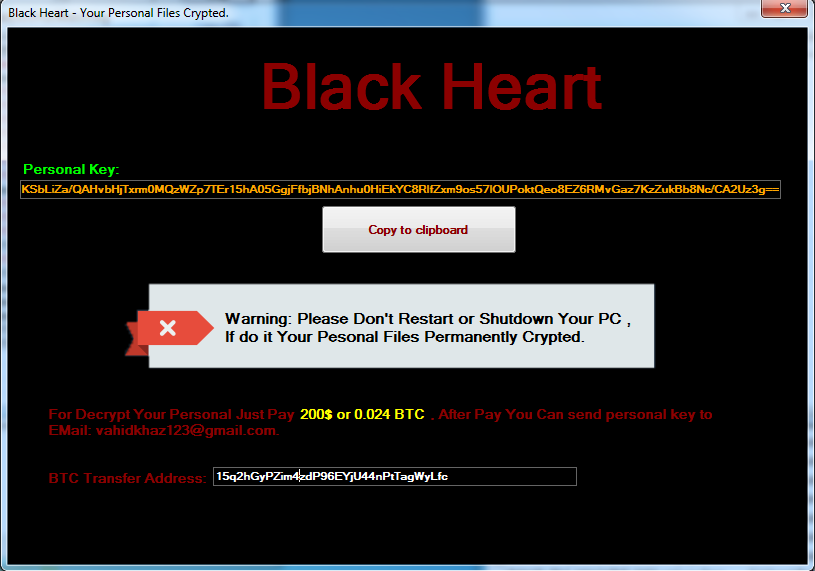
Figure 4 Ransom Message
As shown above, “Ransomware Author” demands for 200$ or 0.024 BTC (In Bitcoins) for decryption and send it to following Bitcoin Address “15q2hGyPZim4zdP96EYjU44nPtTagWyLfc”. It also warns the user if he tries to Shut down or Restart the System, Files will be Permanently Crypted.
Once the payment has been done than user has to send the Email at vahidkhaz123@gmail[.]com containing its Personal Key.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
