Jewsomware Ransomware Overview
Recently, a security researcher has found the new ransomware “Jewsomware Ransomware”.
This ransomware appends the filename of the affected file by adding the .jewsomware extension in the last.
Once the encryption has been completed it shows the ransom note UI on the screen.
As per the ransom note, it demands 300 Euro in the form of BTC in exchange for decryption. If the user didn’t pay at the time of 60 Seconds, it will double the amount of ransom money.
This ransomware tries to fool the users by showing the pop-of Windows Update Message in starting. This ransomware contains some bugs in the code might be due in the development stage.
Flowchart


Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
Technical Analysis of Jewsomware Ransomware
File Name: 1.exe
MD5: 1E96F62785E4B3F4B12813EBD4A6E5A2
SHA1: 3284801095A35511BF512DB171F7600950D8009C
SHA256: 4E63BC54585FB7A70877A96FB9D0B5C12CF56F691FADB37B45986A4AAFC22923
File Type: .EXE
Also, Read:
Detail Description of Jewsomware Ransomware with Screenshots
On execution of this ransomware, it first displays the popup message of debug window that it will start in 20 Seconds

Figure 1Debug Window
Upon clicking the “OK” button after 20 Seconds it will display another Pop-up message box of Windows Update (“Windows will update in 30 Sec & This update doesn’t require a restart”)
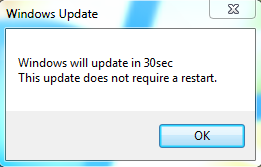
Figure 2 Windows Update
After clicking the “OK” button this ransomware displays the blue screen of fake windows updating.
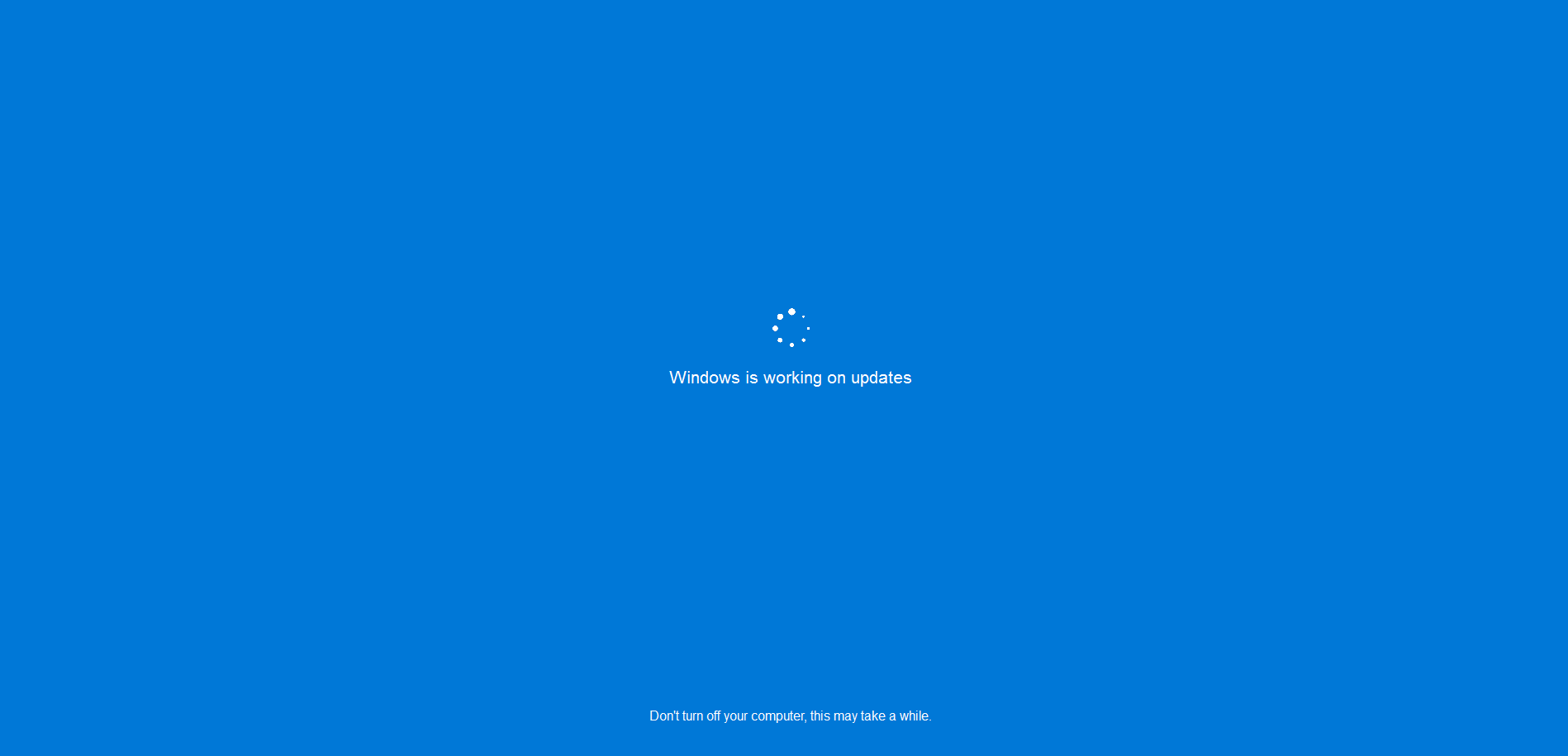
Figure 3 Updating Windows
This ransomware tries to kill the few processes (“Explorer.exe” & “Taskmgr.exe”) in background.
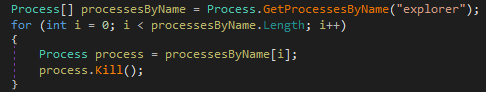
Figure 4 Killing Explorer.exe
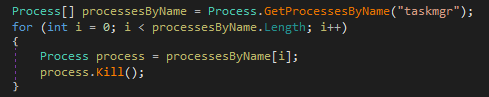
Figure 5 Killing Taskmgr.exe
This ransomware also has the functionality of self-delete.
This ransomware encrypts only those files that matches with its file extensions list. Following is the file extensions list
“.doc .docx .xls .xlsx .ppt .pptx .jpg .jpeg .png .psd .txt .zip .rar .html .php .asp .aspx .mp4 .avi .3gp .wmv .MOV .mp3 .wav .flac .wma .mov .raw .doc .apk .encryptcrypted .ahok”
This ransomware also tries to scan all the drive letters from “A to Z” so that they can infect all the drives on the system with the condition to avoid following folders that contains specific strings in the end
|
Bin
|
Indows
|
Tings
|
System Volume Information
|
Cache
|
|
very
|
rogram Files (x86)
|
rogram Files
|
Boot
|
Efi
|
|
.old
|
|
This ransomware doesn’t delete any Volume Shadow Copies or System Restore Point.
While the ransomware is running in the background it appends the affected filename by adding “.jewsomware” in the last.
As shown below this ransomware has shown their secret key which it’s using in the encryption process.
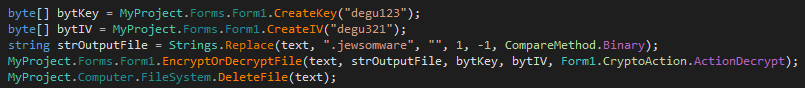
Figure 6 Secret Key
Once the encryption has been completed it shows the following ransom note UI screen on the Victim Desktop Screen (“Your Files Have Been Encrypted by the Sneaky Jew!”)
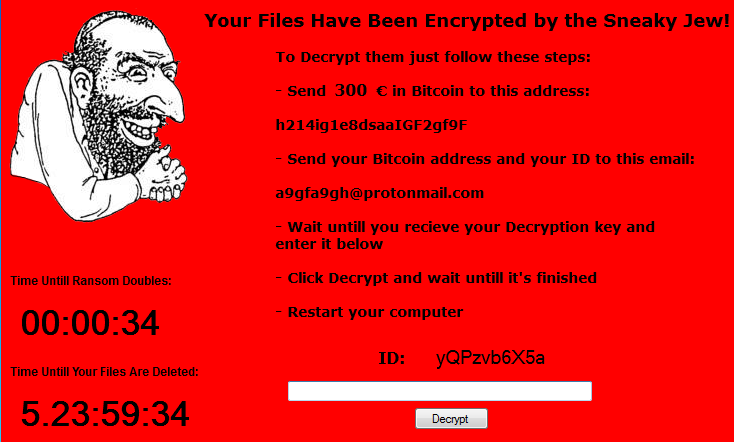
Figure 7 Ransom Note Amount
As shown above, this ransomware runs the countdown timer that doubles ransom amount if the victim didn’t pay in 60 Seconds.

Figure 8 Double Ransom Amount
The funniest part is this when a person tries to delete this window from the taskbar it will restart the same ransom note with the reset timings.
As shown above, another countdown timer is also running that warns the victim has only 6 days to recover the files back from the attacker, after that it will delete the files.
If the victim enters the wrong key it shows the following pop-up window
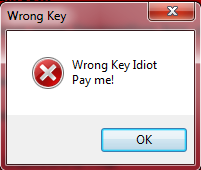
Figure 9 Wrong Key
As shown above, in the ransom note, ransomware creator has mentioned his Bitcoin Address (“h214ig1e8dsaaIGF2gf9F”) & Email Address (“a9gfa9gh@protonmail.com”) to contact them.
Ransomware creator also mentioned the steps after entering the right decryption key.
During analysis we have found that this ransomware didn’t work properly might be due to in development stage and also contains lots of bugs in the code which can be easily rectified by anyone.
By analyzing the code, we are assuming that this code has been written by some script kiddie or newbie.
Are you worried about your PC health?
Check your PC Health for Free!
IOC’s
Associated File Names & Hashes:
MD5: 1E96F62785E4B3F4B12813EBD4A6E5A2
SHA1: 3284801095A35511BF512DB171F7600950D8009C
SHA256: 4E63BC54585FB7A70877A96FB9D0B5C12CF56F691FADB37B45986A4AAFC22923
Associated Contact ID:
a9gfa9gh@protonmail.com
Are you worried about your PC health?
Check your PC Health for Free!
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
