Xmrig.exe - A Bitcoin Miner Trojan In Your Computer!
Xmrig.exe is a bitcoin miner trojan which disrupts all the possible digital currencies and penetrates the system to infect files.
Microsoft has identified it as a PUA such that it hides as xmrig.exe Windows process as PUA:Win32/CoinMiner or Trojan:Win32/Coinminer!bit.
The Xmrig.exe virus causes problems and is not a verified Windows process. The file xmrig.exe trojan is present in the Windows folder and the file sizes on Windows 10/8/7/XP are 2,834,774 bytes, 749,056 bytes, 1,019,392 bytes and 291,183 bytes respectively.
Its file gives us no information about its developer, however, shows that the malicious file is not a Windows core file. The malicious program connects to the Internet or LAN using ports that also help trojan to monitor applications. Therefore, it is essential to remove xmrig.exe from your systems.
How Xmrig CPU Miner Works?
Xmrig.exe trojan miner steals Bitcoin, Monero, DarkNetCoin and other cryptocurrencies with the help of infected files. It starts sharing CPU’s power for its purpose and causes overheating of the processor.

The parasite starts a heavy coin mining process in your system that is used to perform all the accounting processes for a coin platform. Due to the accounting process, your system gets rewarded with digital coins and online money.
However, as your computer is infected, all the money is transferred to the hacker’s wallet, not to you! On the other hand, this process decreases your hardware’s life and the mining doesn’t profit anything to you.
To summarize it, we can say that being infected with the crypto miner trojan you sponsor xmrig CPU miner unknowingly via your system. The whole process is hidden such that neither you know about it nor you have any resources to counter it.
Infection Caused By Xmrig.exe Trojan
When we see our computers getting affected by trojans, we start monitoring the functionality of the computer. The adverse results due to malicious programs and variants are described below.
- Xmrig.exe overloads CPU and decreases the overall performance of your computer.
- The computer boots up for no reason, sometimes freezes while you are working.
- Slow internet browsing speed might cause the internet to stop unexpectedly.
- Fake alert messages and notification pop-ups to update your operating system.
- Irrelevant web search redirects affect your web browsing experience.
- It steals your browsing information and personal data such as IP addresses, banking details, passwords and login credentials.
- Changes your Windows Registry editors to remain undetected from anti-viruses and anti-malware tools.
- Automatic download of executable files from unknown sources and unsecured websites.
- Send fake emails and maintain a false online presence on Social media though you aren’t logged in.
The modifications and unusual activities on the computer let us think upon the solutions of elimination. Solutions in such a way that could bring back our system back to safety.
If you are suffering from the above kinds of symptoms, then our recommendation is to download a removal tool by clicking the below link.

How Did Xmrig CPU Miner Enter Into Your Computer?
Considering xmrig.exe Windows process fake, its easy to assume that it gains entry through source programs carrying a payload of the cyber threat. Furthermore, without your permission, it gets installed into your computer automatically. Few sources of such programs are:
- Malicious websites specifically designed to inject Trojans
- Legitimate websites infected with Trojans
- Email attachments and infected links
- Fake updates for installed software
- Peer-to-peer sharing software
- Malicious video players, audio players and codecs in computer
- Free downloadable games and programs (freeware)
- Chat applications
- Malicious Social media links directing to infected files and websites
Therefore, it is important to remove it and for that, we must block the above entry paths that are responsible for injecting threats.
Automatic Method: Prevent Xmrig.exe Trojan Infection
An automatic scan of anti-malware tool finds out the presence of all unwanted programs and files. Its robust technology prevents the threat from collecting your information and remove the xmrig.exe virus.
Malware Crusher is one such tool that has different threat removal capabilities like;
- It’s real-time protection feature, performs a deep scan, detects malicious software and infected files within your system.
- The Quarantine feature of the tool removes all infected files from your computer in addition to keeping a record of all deleted malicious program.
- Malware Crusher becomes fiercer in detecting keylogging, remote connections and saving your session data from being recorded.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities.
- The 24X7 online protective shield works as an anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
The automatic method Malware Crusher no doubt is the best option to easily remove (uninstall) cyber threats and other installed malicious codes, programs from your computer.
However, you can also take a look at the manual removal process of virus given below.
How To Remove Xmrig.exe Trojan Miner From System Manually?
The infection is specifically designed for crypto mining and it is difficult to stop the entry of threats associated with the trojan. Anyhow, you will always encounter threats somewhere on the internet as their intention would always be to collect your data.
To avoid this situation, you can use the manual xmrig.exe virus removal process which is described below;
- In your windows computer, press Ctrl + Shift + Esc to open Task Manager.
- Find all and select suspicious, not useable programs. Right click on the selected choice and click End Task.
From the above image, you can gather that other than Google, no other program is running. But, if in your task manager window you find something suspicious, then end it. Also, try uninstalling it through our removal process.
Uninstall Suspicious Files
Uninstalling suspicious variants is our second step after stopping all processes. For this press Windows Key + R, it opens a Run Window.
- Now type appwiz.cpl to open Programs and Features window.
- Select the suspicious program and uninstall it.
Remember to choose only those programs which in your choice could be harmful to your computer. It is a tricky step because you cannot randomly select any program and uninstall it.
Here, we would say a robust anti-trojan tool is easy to use in comparison to the manual process.

Remove Malicious Browser Extensions
If you think that uninstalling the programs from your computer helps you to get rid of threats, then you are wrong! You must remove malicious extensions by yourself.
1. Click on the Customize and control menu icon at the top right corner of Google Chrome.
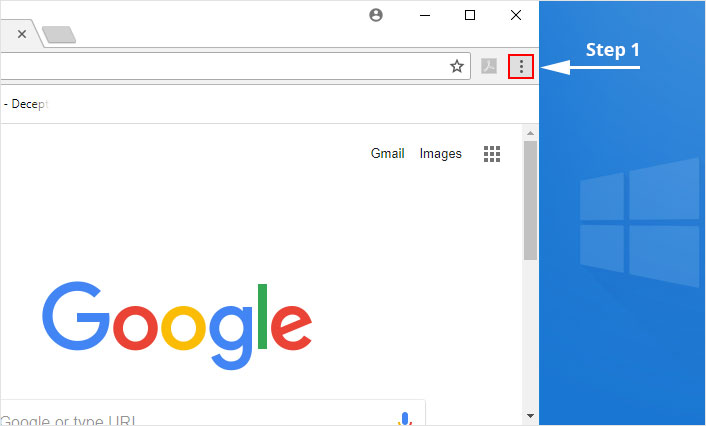
2. Select "More tools" from the menu.
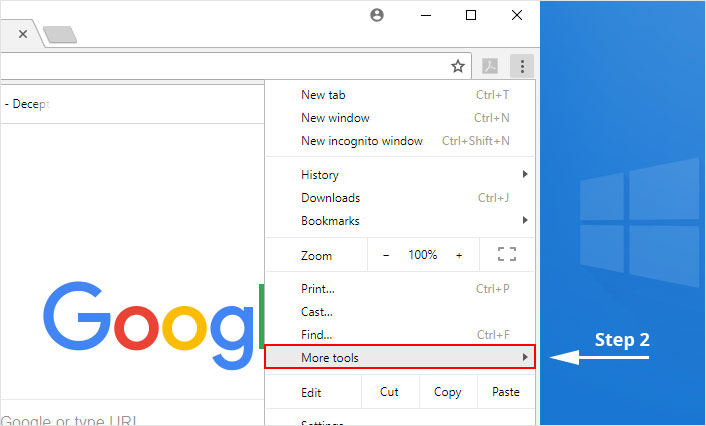
3. Select "Extensions" from the side menu.
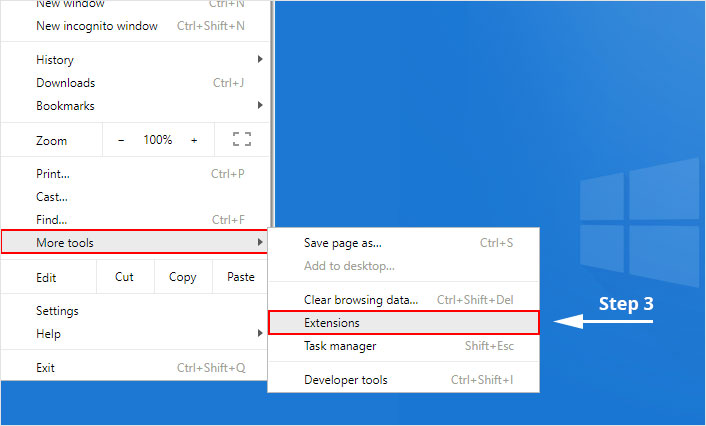
4. Click the remove button next to the extension you wish to remove.
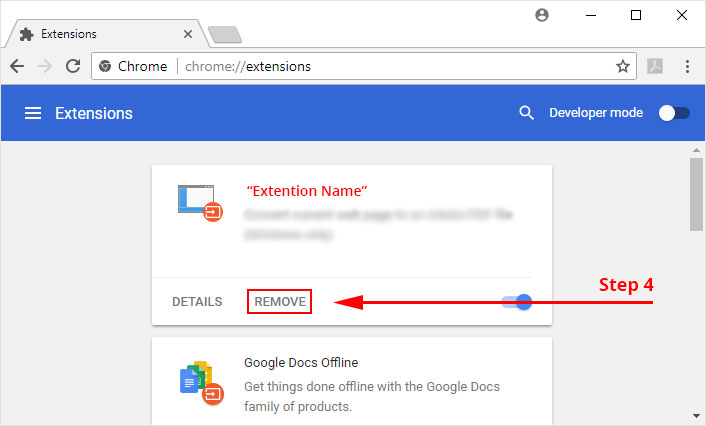
5. It will confirm again, click “remove” and the extension is finally out of the system.
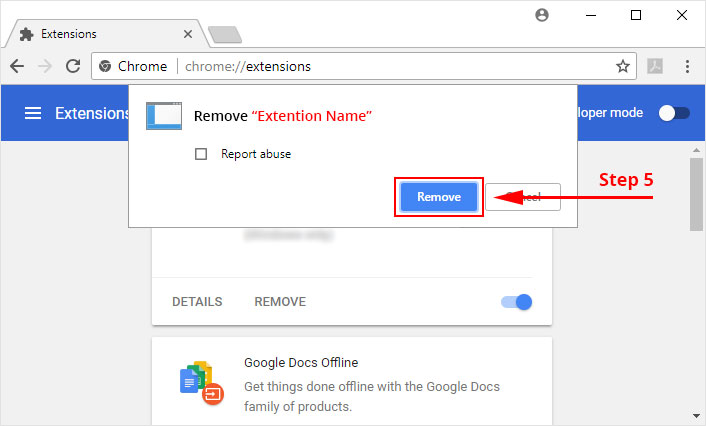
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
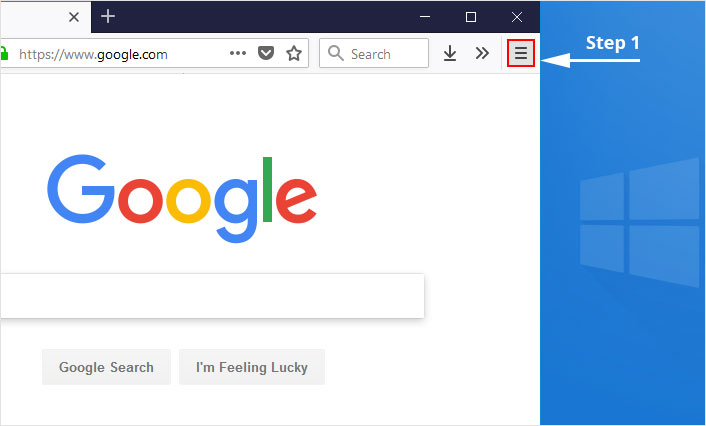
1. Click on the “menu” button at the top right corner.
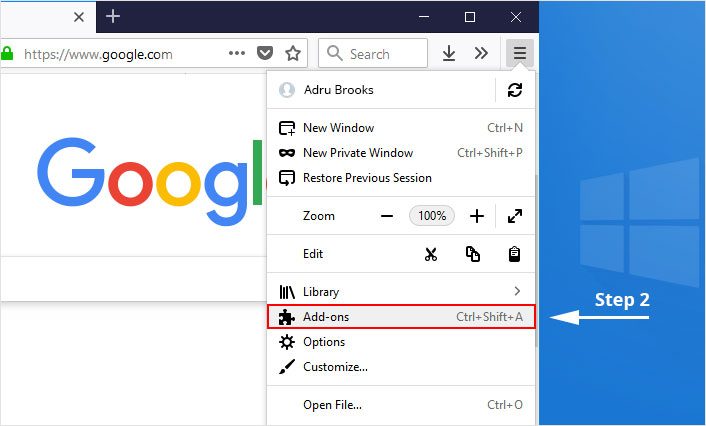
2. Select “Add-ons” from the menu.
3. Click the “Remove” button next to the extension you wish to get rid of.
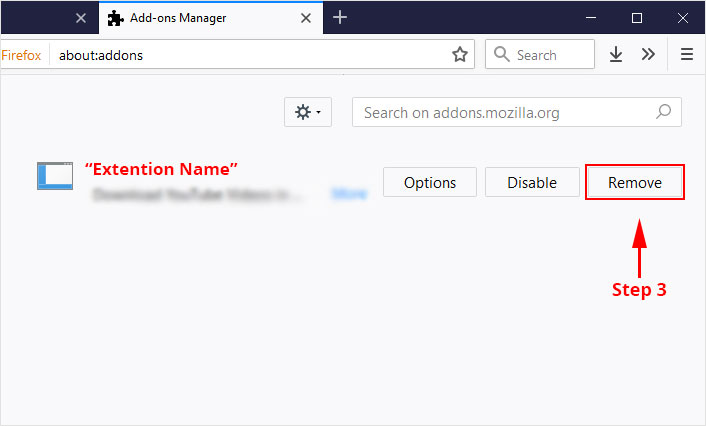
Now that we have successfully eliminated the malicious browser extension, we need to create a robust firewall to avoid any such thing that makes our system and privacy vulnerable to various online threats.
However, if it becomes difficult for you to judge extensions, we recommend you to reset your browser settings.
Reset Browser Settings
Before you set your browser to default, delete your search history including passwords and login credentials. (Better you note down your personal info on paper before deleting it.)
Reset Google Chrome
- Click three dots on Chrome Window.
- Select Settings, scroll down to the bottom of the page and click Advanced.
- Again scroll down to the end, click Restore settings to their original defaults > Reset Settings.
Reset Mozilla Firefox
- Open Firefox Menu (in the right corner of the Window)
- Select Help > Troubleshooting Information > Refresh Firefox > Finish.
- You can also try Safe Mode to disable the add-on.
Reset Internet Explorer
- Click Gear-icon on the right corner of IE.
- Select Internet Options > Advanced and select options, click Reset.
The manual process is lengthy, needs technical knowledge to remove viruses and trojans from your Windows OS. Though you can execute each step, locating malicious files, extensions and program related to the xmrig.exe trojan miner is a difficult task.

Thus, a permanent solution is needed which can fight 24x7 whether you access your system or not. To get rid of the trojan, you must download Malware Crusher, install it and perform a quick full scan.
It automatically removes Xmrig and fixes your windows computer in less than 5 minutes.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
