RedBoot Ransomware Encrypt Files and Modifies Hard Drive Permanently
A newly discovered Redboot Ransomware modifies MBR, encrypt files and damages your hard drive permanently.
Redboot encrypt files and was first detected on September 23, 2017. It's a bootlocker ransomware that doesn’t provide any input key to get your system back.
The distribution methods are currently not available and it majorly targets computer system of Windows OS.
Unfortunately, a ransomware attack implications are beyond the cost of the ransom and it could let you face;
- Cost of replacing compromised devices
- Loss of proprietary data
- System downtime, which affects the ability to operate
- Reputational damage
- Potential legal penalties arising from poor security or handling of data
The file encryption operation is similar to Petya Ransomware that encrypts executables and DLLs including normal regular data files, eventually portraying the infected machine useless.
How RedBoot Enters System and Encrypt Files?
Call it as a Night of the Devil, RedBoot ransomware or Wiper has already hit more than 65 countries where victims couldn’t restore .locked files.
Cybersecurity experts say that the RedBoot Ransomware is still a test version and is not deploying full attack. It targets files such as video, audio, music, text files, databases, configuration files, etc. Few typical examples of file extnsions are as follows:
.swf, .sav, .tiff, .db, .dbf, .djvu, .dbx, .rar, .rtf, .scr, .dat, .cdr, .cer, .chm, .conf, .dwg, .drw, .casb, .ccp, .cal, .cmx, .cr2, .py, .asm, .mht, .mobi .mhtm, .mkv.

RedBoot's current version is a compiled AutoIT executable that extracts into five different components:
- boot.asm is an assembly file compiled into the new MBR. On compilation, it generates the boot.bin file.
- assembler.exe is a renamed copy of nasm.exe that compiles the boot.asm assembly file into the boot.bin file.
- main.exe is a user mode encrypter that encrypts the files on the victimized computer.
- overwrite.exe overwrites the MBR with the newly compiled boot.bin file.
- protect.exe terminates and prevent running various programs such as the task manager and process hacker.
Once boot.bin is compiled, the launcher deletes the executable assembly files, then use the overwrite.exe program with the compiled boot.bin with this command:
“[Downloaded_Folder]\70945836\overwrite.exe" "[Downloaded_Folder]\70945836\boot.bin”
While the main.exe is encrypting files, it appends the .locked extension onto each encrypted file's filename.
Now the computer redboots the computer instead of starting and displays a ransom note. While the ransomware is a brand new, it does not look promising at all to the victims.
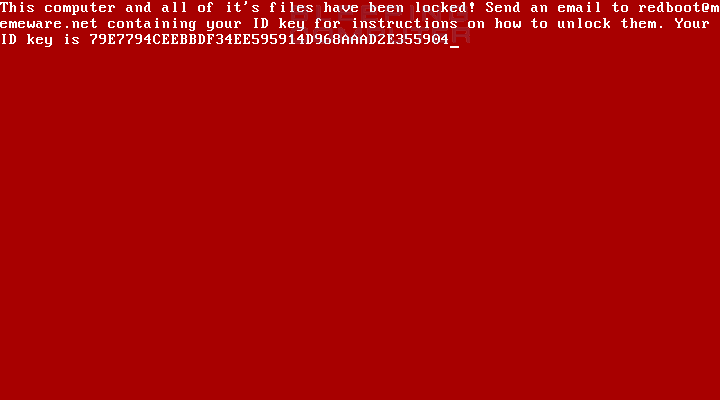
Even if the victim contacts the developer and pays the ransom, the hard drive may not be recovered. If anything changes with this analysis I will make sure to update the article to provide more information.
Bad guys are regularly updating existing ransomware variants some famous examples of such updated ransomware are Wannacry assault, .Arena attack, Scarab .Skype, Pegasus spyware, SamSam, etc.
Impacts Of Redboot Ransomware
It quickly spreads through spam emails, websites, peer to peer file sharing, freeware, cracked or pirated software and social hijacking. It degrades the computer performance and compels you to pay money for your own files within some time limit.
Once victimized, the ransomware attacks your system and web browsers settings in the following ways;
- It consumes high CPU power and lowers down the overall performance of your computer.
- The computer boots up for no reason, freezes while you are working.
- Slow internet browsing speed might cause the internet to stop unexpectedly.
- Fake alert messages and notifications pop-ups to asking you to pay the ransom.
- It leads to irrelevant web search redirections and highly affects your web browsing experience.
- It steals your browsing information and personal data such as IP addresses, banking details, passwords and login credentials.
- It also changes your Windows Registry editors to remain undetected from anti-viruses and anti-malware. Automatic download of executable files from unknown sources and unsecured websites.
- Sending emails and maintaining your online presence on Social media though you aren’t logged in.
Cybercriminals via these threats steal information like IP address, URL’s Search, browser history, search queries, username, ID, passwords, banking information and ATM Card information.
Though ransomware removal is a complicated task, it is achievable via decrypt .locked files and restore .locked files.
Is RedBoot really a Wiper?
While this ransomware performs standard user mode of encryption and does modify partition in hard drive, there is no way of inputting a redboot ransomware file recovery key to recover your system. Thus, we may indicate that it is a wiper disguised as ransomware.
So it is hard to tell whether it is buggy ransomware or wiper disguised as one?
If you do not have any security software, then download a reliable software for Redboot ransomware removal. However, before that, you can use a few manual methods to see whether they can work against ransomware or not.
Temporarily Disable Redboot Ransomware
Windows Safe Mode Options
Steps to be followed to enter the safe mode Win XP/Vista/7.
- Click start, then shutdown, then restart.
- While the computer is booting up at the very first screen start tapping F8 until you see the advanced boot options.
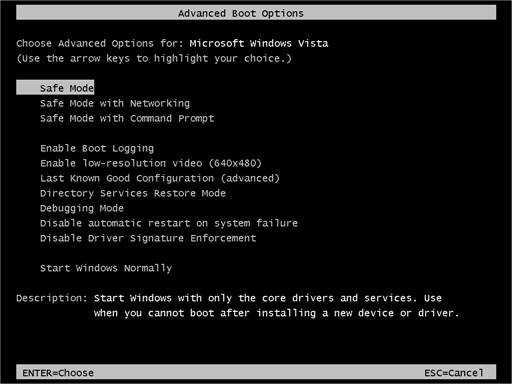
- In the advanced boot option’s, you need to select safe mode with Command prompt from the list of given options.
Steps to be followed to enter safe mode in Win 8/10.
- On the windows login screen, you need to press the power option.
- Now, press and hold the shift key on the keyboard, and then click Restart.
- Now, among the list of options you need to select Troubleshoot, and then advanced options, then startup settings and finally press restart.
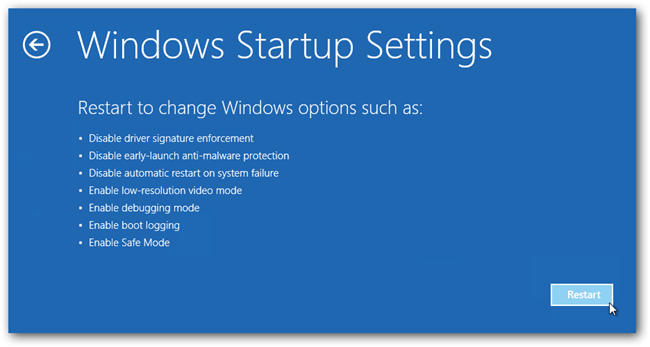
- Once your computer restarts and gives you the list of startup options you need to select Enable Safe Mode with Command prompt.
Windows System Restore
- Once you see the command prompt windows, type in cd restore and hit enter on the keyboard.
- Now, type rstrui.exe and hit Enter again.
- Then you would see new windows, click on next over there and select a restore point that is before the date of infection.
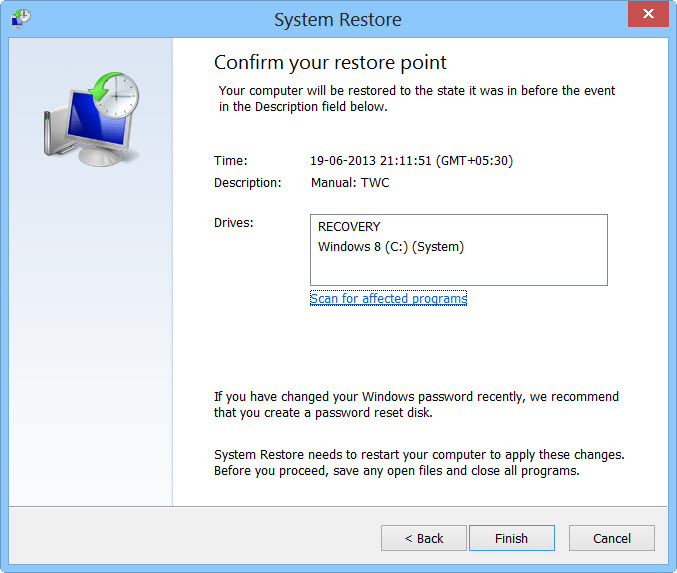
- Then, click next and followed by yes.
But here's something you should never forget: Following these steps, you might get rid of the malware from your PC and restore admin rights, but it won't decode your documents.
After temporarily disabling the ransomware, we need to create a secure firewall to fight against such intrusions and prevent them in the future. For this, you must follow the automatic redboot ransomware removal tool guide.
RedBoot Ransomware Removal Tool: Malware Crusher
You see a ransomware note after the ransomware infects your system. Instead of paying the ransom you try to solve the issue by uninstalling and removing unwanted programs, registry file editors from your operating system. However, you don't get success and redboot remains on your computer.
The reason is Encryption - Decryption technique! The ransomware encryption of your files and doesn't allow to access them anymore. That’s why locked files are decrypted using genuine cybersecurity tool.
Malware Crusher is one of those with which your question: “how to remove redboot ransomware?” must end. Use this redboot ransomware decrypt tool before it collects your information and money.
It can be your permanent ally due to its following removal capabilities;
- It’s a real-time protection feature, performs a deep scan, detects malicious software, infected encrypted files within your system.
- The Quarantine feature of the tool removes all infected files from your computer in addition to keeping a record of all deleted malicious program.
- Malware Crusher also creates a shield against Ransomware, Adware, Malware, Browser Hijackers, Viruses, Extensions and Trojans from entering into your system.
- The 24X7 online protective shield works as anti-exploit technology and blocks the ransomware component before they hold files as a hostage.
- Malware Crusher tirelessly visits all domains, URLs and web pages to secure your online presence from fraudulent entities.

We also recommend you to use a cloud storage facility that has high-level encryption and better multiple-level authentication.
To get a better security awareness on cybersecurity threats keep visiting us, forget not to download Malware Crusher. Its 5-minute function could be a savior for your Windows computer.
Tips to Prevent virus and malware from Infecting Your System:
- Enable your popup blocker: Pop-ups and ads on the websites are the most adoptable tactic used by cybercriminals or developers with the core intention to spread malicious programs.
So, avoid clicking uncertain sites, software offers, pop-ups etc. and Install a powerful ad- blocker for Chrome, Mozilla, and IE
- Keep your Windows Updated: To avoid such infections, we recommend that you should always keep your system updated through automatic windows update.By doing this you can keep your device free from virus.According to the survey, outdated/older versions of Windows operating system are an easy target.
- Third-party installation: Try to avoid freeware download websites as they usually install bundled of software with any installer or stub file.
- Regular Backup: Regular and periodical backup helps you to keep your data safe in case the system is infected by any kind of virus or any other infection.Thus always backup important files regularly on a cloud drive or an external hard drive.
- Always have an Anti-Virus: Precaution is better than cure. We recommend that you install an antivirus like ITL Total Security or a good Malware Removal Tool like Download Virus RemovalTool
