Chrome Bug Exposes Users’ Facebook Information
A new Chrome Bug is allowing hackers to access your private information from Facebook, Google, and other websites. The security flaws will affect only those who are not running the latest version of Chrome.

A few days back Google marked all non HTTPS websites as ‘Not Secure.’ With the release of Chrome 68, the web is now a more secure place for the internet users.
Ron Massas, a security researcher from Imperva, discovered
A vulnerability CVE-2018-6177 in Google browsers allow attackers to know about you from websites and social media platform.
CVE-2018-6177 takes advantage of weak audio/video HTML tags and affects Google browser powered by Blink Engine.
For example, Facebook a social media platform collects in-depth profiling information of its users. The information like age, gender, location, interest, etc. allow users to define target audience under Facebook post targeting feature.
How does the Browser Attack work?
As the HTML tags are weak, hackers insert audio and video tags and note the response of Chrome received from Facebook and other websites.
The responses don’t reveal any data about you but ask you a series of yes/no questions. The bug then mines our private data by asking questions such as in games like ‘20 Questions.’
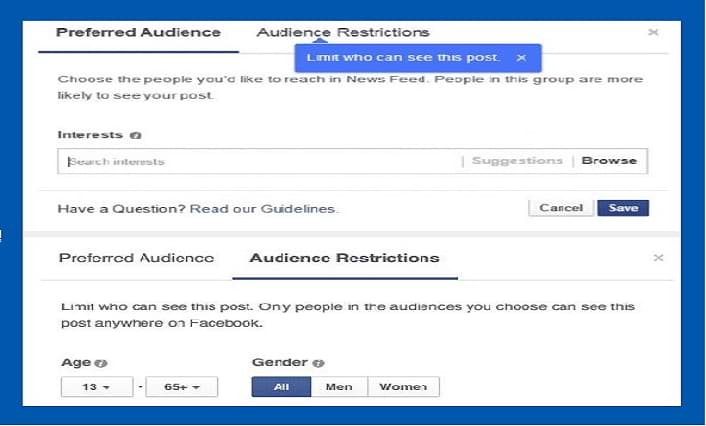
Now, if a website embeds Facebook posts on a web page, it loads only a few specific posts based on individuals’ profile data and targeted audience settings.
For example, a post related to hacking and information security is visible only to the male Facebook users of age 26. With the help of CVE-2018-6177, a hacker gets personal information from visitors, regardless of their privacy settings.
The attack sounds simple, but site administrator can’t determine whether the embedded post was loaded successfully for a particular visitor or not.
Audio and video HTML tags don’t validate the content type of fetched resources. Thus, an attacker uses multiple hidden video or audio tags on any website to request the Facebook posts.
With this vulnerability in the browser, the attacker-controlled website measures the size of cross-origin resources through java scripts. CORS is a browser security mechanism which prevents a site from reading the content of other websites without permission.
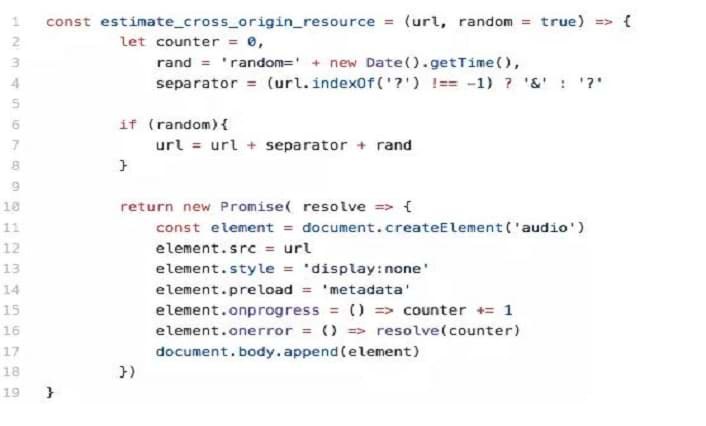
Attacks are even more severe on sites which need email registration such as shopping sites, payment gateways, etc. The vulnerability CVE-2018-6177 also works against websites using APIs to fetch session specific information.

Get peace of mind! Get rid of malicious programs instantly
Free Checkup & fix for your PC! Get rid of malicious programs instantly!
How to Stop Browser Attacks?
Nearly 60% of people are using Chrome Browser; therefore, the problem is more significant than it looks. Tech giant, Google released a patch to fix the bug in Chrome 68. Hence the expert advice is to update Google chrome into the latest version.
Update Chrome on the computer
- Open Chrome.
- Click More (the icon made up of three dots at top right)
- Click Update Google Chrome. However, if you don't see this button, you have the latest version otherwise Chrome will update.
- Click Relaunch.
Update Chrome on Android
- Go to Play Store app.
- Tap Menu > My apps & games. You will get a list of apps which need updates.
- Look for Chrome and tap Update.
Update Chrome on iPhone and iPad (MAC/iOS)
- On your iPhone or iPad, open the App Store.
- At the bottom, tap Updates.
- Go to pending updates and look for Chrome.
- Tap Update to install the new version of Chrome.
- If Apple ID password is asked, enter it. Update and install your Chrome.
A member from Google Security said;
“Several javascript runs at a time and each test different restrictions which favor attackers and hackers. However, by engineering sites for each restriction, the extraction of users' private information could be stopped. It is only possible with new Chrome version 68.”
Are you worried about your PC health?
Check your PC Health for Free!
